-
Posts
939 -
Joined
-
Last visited
-
Days Won
22
Posts posted by i8igmac
-
-
my understanding.
If eth0 is up and working, then you launch wpa_supplicant -iwlan0
Eth0 gateway ->192.168.0.1
Wlan0 gateway->10.0.0.1
You will notice eth0 is still the active connection. route -n will show the gatway is still 192.168.0.... I can change this with ip route gw add via 10.0.0.1.
so, what service or config is responsible for device priority? eth0>wlan0
-
my understanding.
If eth0 is up and working, then you launch wpa_supplicant -iwlan0
Eth0 gateway ->192.168.0.1
Wlan0 gateway->10.0.0.1
You will notice eth0 is still the active connection. route -n will show the gatway is still 192.168.0.... I can change this with ip route gw add via 10.0.0.1.
so, what service or config is responsible for device priority? eth0>wlan0
-
-
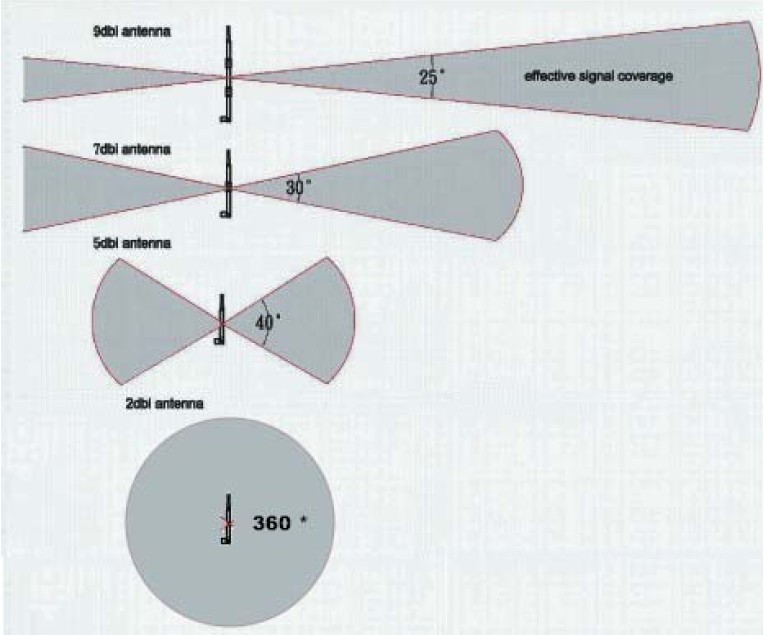
if you remove a antenna while the device is still powered on, I think Andrew McNeill has said this may cause damage to the radio...
I may have experienced this kind of damage when building my own antennas... but its hard to say the exact cause in my situation... if you see zero access points then I would say this damage is permanent...
Bigger Xdbi Omni directional antennas, work very well in the right situation... you will achieve much farther distance but line of site matters greatly. Every wall or object will effect the signal, even rain fall can effect your signal when dealing with great distances...
if you look at your smaller dipole antenna, it will produce a invisible radiation Bubble... this big bubble can cover multiple floors very well because of its height and width.
If you look at a 9dbi omni directional antenna, it will produce the Same amount of radiation but squeeze this bubble into a pancake and now you can cover a greater distance but no longer reach the second floor of a building...
Maybe look into directional or semi directional
-
 1
1
-
-
http://www.npr.org/sections/money/2014/05/30/317074394/drone-wars-who-owns-the-air
I don't mean to hijack a post but.
"he who owns the soil owns up to the heavens "
This rule can win a disputed in court about a persons tree growing over your property and damage done to your landscape...
So, what about other people's wifi signal reaching my airspace? I do own proprty and feel if its invading my property, I can crack it all day long?
-
I would suggest virtual machine or vbox hosting all your virtual machines...
I like vbox. There are options for adjusting ram size and cpu...
-
do you have a list of os you plan to run?
-
How do I summon the geniuses.
-
i have been manually writing wpa.configs for use with wpa_supplicant for a while now, and i find its a headache
this process is almost a guessing game, i dont see much documentation on this subject other then copy and paste a config found online and hope it works, if it fails then modification is needed...
If there are any opinions on building these wpa configs, maybe more command line tools to help automate this process, plz share...
So, i feel that all the information you need to properly build a config is available by running `iwlist wlan0 scan`
So, here is a little ruby script... your wireless card must be UP and in manage mode...
this script will filter out a bunch of junk you dont need to see...
there are 2 variables to pass to the script, wlan0 and STRING
the string can be anything you find in the output of iwlist scan, like a mac address or essid name...
root@debian:~/project# ruby iwlist.rb wlan0 HOME-7
identicle results can be seen with a simple grep command
iwlist wlan0 scan | grep -v Unknown
puts "device: #{ARGV[0]}" puts "essid: #{ARGV[1]}" data=`iwlist #{ARGV[0]} scan`.gsub("Cell ", "\n\n") data.split("\n\n").each{|x| if x.include?("#{ARGV[1]}") x.each_line{|x| if not x.include?("Unknown:") puts x end } end }And here is the example output you will see below... and how i run the script...
root@debian:~/project# ruby iwlist.rb wlan0 HOME-7
22 - Address: 00:26:F3:58:7E:C8 Channel:11 Frequency:2.462 GHz (Channel 11) Quality=27/70 Signal level=-83 dBm Encryption key:on ESSID:"HOME-7EC8" Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/s; 9 Mb/s 18 Mb/s; 36 Mb/s; 54 Mb/s Bit Rates:6 Mb/s; 12 Mb/s; 24 Mb/s; 48 Mb/s Mode:Master Extra:tsf=000000a05f2d0146 Extra: Last beacon: 230ms ago IE: IEEE 802.11i/WPA2 Version 1 Group Cipher : CCMP Pairwise Ciphers (1) : CCMP Authentication Suites (1) : PSKSo, now we can see this access point uses WPA2 version 1
the protocal=WPA2
the Group cipher=CCMP
the Pairwise cipher=CCMP
authentication is PSK
and here is how i would think a wpa_supplicant config should look like...
ctrl_interface=/var/run/wpa_supplicant ap_scan=0 network={ ssid="HOME-7EC8" psk="H2110413F11C8BF7" #psk=57996240 proto=WPA2 key_mgmt=WPA-PSK pairwise=CCMP group=CCMP }Does this look correct? currently im getting a authentication timeout error witch might only be due to signal strength...
each access point will show different kinds of encryption requirements that are displayed from iwlist scan... here is a example of what I THINK is backwards compatibility, what i mean by that is this next access point will support clients for WPA2 version1 and wpa version1
ruby iwlist.rb wlan1
15 - Address: 40:4A:03:C3:D6:B5 Channel:11 Frequency:2.462 GHz (Channel 11) Quality=55/70 Signal level=-55 dBm Encryption key:on ESSID:"myqwest6671" Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/s Bit Rates:6 Mb/s; 9 Mb/s; 12 Mb/s; 18 Mb/s; 24 Mb/s 36 Mb/s; 48 Mb/s; 54 Mb/s Mode:Master Extra:tsf=000001cb08c4c236 Extra: Last beacon: 260ms ago IE: IEEE 802.11i/WPA2 Version 1 Group Cipher : TKIP Pairwise Ciphers (2) : CCMP TKIP Authentication Suites (1) : PSK IE: WPA Version 1 Group Cipher : TKIP Pairwise Ciphers (2) : CCMP TKIP Authentication Suites (1) : PSKyou can see this access point might allow wpa and wpa2 protocol...
here is the best document if can find online for a reference https://w1.fi/cgit/hostap/plain/wpa_supplicant/wpa_supplicant.conf
-
That is the p01? By mistake I got a e02...
mine does not have sata or mini pcie, does yours?
I purchased a 8gig ssd from Amazon I planned on trying to place the ssd inside the plastic case... the ssd was like. 10$ I planned on installing debian to the ssd...
-
What model pogo? I might buy a couple more, I want to see the boards. I hope I have better luck...
-
Euuuu. I have a pogoplug in one of my junk boxes. Horrible things. Flakey as hell.
did you install debian? the default firmware/software is crap... good concept but i read a lot of unhappy people...
a simple ftp server would replace the pogoplug software just fine...
so far i can see its potential, this device can supply power to lots of hard drives, so a few wireless cards is no porblem (i assume)
ill look into installing aircrack soon.
-
i have just purchased and recieved a pogoplug... just installed debian... kinda of a pain because of all the outdated blogs and i wanted to post a working link...
first install uboot and then install the debian system
http://blog.qnology.com/2014/07/hacking-pogoplug-v4-series-4-and-mobile.html
apt-get install aircrack-ng <--- fail
apt-get install reaver worked lol
http://ftp.us.debian.org/debian/pool/non-free/f/firmware-nonfree/?C=M;O=D
atheros-2016*.deb
wireless install
aircrack install,
https://scottlinux.com/2012/01/13/install-aircrack-ng-on-debian-linux/
install what ever is missing...
apt-get install libnl-dev
-
can I ask you to post only the raw data. Exclude all the junk wireshark includes...
the session id can be a little tricky, it may need to be revalidated after every attempt...
how does the server respond when a successful login happens? 302 ok?
how does the server respond when I fail login happens?403 forbidden?
how does the web server respond when you fail to produce a proper post requests?400 bad request?
there may also be firewall rules! when so many failed login attempts happen, the web server may change how it responds to successful login! Meaning that even though you have supplied the correct creds, the server responds with a 403..
I have never seen a router have any kind of firewall rules to protect any of its services, at least none that exist in peoples homes...
I had a project that I scrapped all the default router user:passwords combinat into a word list... I'm not sure where I placed it...
list all the ports, telnet maybe easier to brute..
-
press the little red reset button on the machine...
As for a brute force. Start up wireshark and attempt a login, copy the POST request and paste here... you can also record the same login attempt for telnet...root:root
there is alot more to a brute force then just starting up hydra...
Those exploits don't seem useful in your situation
-
If the access point is unresponsive and no pins are exchanged... I would think the access point is not vulnerable or out of range...
-
I would also remind the people that internet explorer is the most targeted piece of software.
0-day for ie go to the highest bidder (US government)
-
Sounds like alot of fun. I would love to be appart of something like this and get paid big bucks lol...
I would suggest a noscript plugin( not sure if available for ie ) and a training class on how it works... not sure if something like this is applicable...
firewall rules for the win.
-
are there any kinds of logs related to get requests you can dig threw? You can try to setup burp suite as the proxy to give you a visual... if you can recreate the crash...
I use tcpick daily, a console application I like filter threw live stream...
You could search threw traffic.pcaps for strings related to the crash log...
I believe this stuff comes from a compromised add's campaign , to deliver exploits to a trusted domain's viewers ...
-
Could this be a flash player exploit? Can you find the exploit code (if any) can you reproduce the crash?
-
http://thehackernews.com/2016/02/facebook-france.html?m=1
good read and related to this conversation
-
we are all creatures of habit.
I check my facebook
I check hak5
I check thehacker news
I check kickasstorrent
I check my email
These kinds of patterns are identifiable, every search i made on amazon, youtube, google are all identifiable...
I guess I'm just agreeing with Cooper but pointing out the ability to identify the habit of the creature
-
have you found any tools left behind? A virus scan might show the location where the guy made him self feel at home...
Try to recover deleted files from the locations discovered...
This sounds like alot of fun... I'm sure a publicly available tool was uploaded to the windows 7 machine to crack the password. But the exploits used would be exciting to hunt down... or what if it was done from a person in the building... boot up the windows 7 machine with kali and give me ssh :-)
-
follow arpspoof tutorial... install the suite by apt-get install dsniff
arpspoof 192.168.0.1 -t 192.168.0.111
arpspoof 192.168.0.111 -t 192.168.0.1
192.168.0.1= router
192.168.0.111=server
enable ip forwarding on your distro.
Then use some ip tables to control all traffic on port 80, 8080, 443 to a proxy like squid...
learn it...




debian networking services. device priority. eth0>wlan
in Questions
Posted
I have 2 systems that share the same situation... (I'm sure all linux will do this)
Debian arm version 2016
network-manager was not present but I see networking service. It fails to stop when I run service stop (witch was frustrating)
I had hopes to find exactly what controls this priority scenario...
If eth0 is associated then Hold this gateway. what if eth0 does not provide internet? Its still the priority over any other device!
In my situation, eth0 is simply providing me remote access via ssh server...
(I wont be able to. Test your commands until I get home)