-
Posts
21 -
Joined
-
Last visited
Posts posted by ghostheadx2
-
-
If possible, I want another form of MITM besides SSL stripping.
-
SSL stripping no longer works. I've been researching but gotten little results as to tutorials for other types of infusions. I want to get an infusion that can either get me wifi passwords or passwords to someone's accounts as they log into them. If possible, I would like some er infusions to start with downloading. I tried the wps infusion and it didn't work well with my router (which is why I want to use RubyReaver or Auto-Reaver). So, what other infusions could be used to monitor my other computer's web activities and the passwords that I get when I log in with my other computer (that I'm using as a target)? If possible, it would be nice if it was something I could use information I get from the PineAP log and input into such an infusion to get my passwords. I learned from this video about how to use the pineAP:
https://www.youtube.com/watch?v=IdhuX4BEK6s&index=2&list=PLuXfzxj2yX_uCE8dPbP39rQIB0a8PkFHT
So yeah, I don't want to buy too many new devices. I want to rely on my pineapple, but if possible I might want the documentation or something similar to learn to use such infusions. I might plug a wireless modem into my pineapple someday and go wardriving, but I want to learn to hack my own wifi first to learn before I go wardriving.
-
I think this is a completely different subject from the previous thread, so forgive me is this is double posting. I found this program called auto-reaver for backtrack:
https://code.google.com/p/auto-reaver/
I edited it, changing the mon0 to wlan0mon in one of the scripts, titled "wash". I'm trying to edit it to work with kali 2.0. I did what one of the guys in this thread did:
https://forums.kali.org/showthread.php?19641-Reaver-WPS-Locked-Situation-and-Useful-Link/page4
And I quote:Further debugging of autoReaver
When we tried to run autoReaver in a Hard drive install of Kali-linux 1.07 we were unable to install
apt-get install original-awk
apt-get install gawk
We got warnings that mawk was in residence and when we tested autoReaver against real AP targets we got numerous gawk line errors. To solve this we changed all gawk entries to mawk. We left awk entries in place. The program ran fine after that.
Note this only applied to our HD install.
MTF
I know how to do the first part of that and I did. I did both commands. But I'm lost as to how to change all gawk entries to mawk. I'll research it, but I'm asking because when I look at the script, I don't want to screw up the script as is. I want to edit it correctly. There are also some changes I think need to be made to make this backtrack program work for kali 2.0. Could someone explain what I need to read or how to change this properly to fit kali 2.0? There are various scripts. -
for me it tries the same pin over and over. how do I change the arguments so it doesn't ignore it and tries a new pin even if it doesn't get a nack
-
So, when I try this command:
root@blackJesus:~# giskismet -csv ./Clarendon_Pineapple1-01.kismet.csv Unable to open ./Clarendon_Pineapple1-01.kismet.csv root@blackJesus:~# giskismet -csv ./Clarendon_Pineapple1-01.kismet Unable to open ./Clarendon_Pineapple1-01.kismet root@blackJesus:~# giskismet -csv ./Clarendon_Pineapple1.kismet.csv Unable to open ./Clarendon_Pineapple1.kismet.csv [/code] #I end up not being able to store results from my pineapple into a SQLite database. Here's what I'm doing before hand: [code] CH 5 ][ Elapsed: 6 s ][ 2015-12-28 22:15 BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID 34:12:98:08:25:44 -47 0 1 0 3 -1 WPA <length: 0> 00:25:00:FF:94:73 -1 0 0 0 -1 -1 <length: 0> 28:C6:8E:84:A1:FC -20 13 5 1 1 54e WPA2 CCMP PSK boogieboardb 94:F6:65:D6:EE:78 -45 3 0 0 1 54e. WPA2 CCMP PSK PALMER 36:44:25:08:98:10 -46 2 0 0 1 54e WPA2 CCMP PSK boogieboardb 02:13:37:A5:5D:22 -59 19 1 0 6 54e. WPA2 CCMP PSK Free Wifi 94:F6:65:56:4D:88 -58 8 0 0 11 54e. WPA2 CCMP PSK AV Wireless 94:F6:65:96:4D:88 -59 8 0 0 11 54e. WPA2 CCMP PSK Guest Wirele 94:F6:65:D6:4D:88 -57 7 0 0 11 54e. WPA2 CCMP PSK PALMER 88:1F:A1:32:3D:74 -62 10 0 0 1 54e WPA2 CCMP PSK Sierra 94:F6:65:16:4D:88 -63 11 0 0 11 54e. WPA2 CCMP PSK Data Wireles 94:F6:65:17:88:D8 -62 3 0 0 1 54e. WPA2 CCMP PSK Data Wireles 94:F6:65:D7:88:D8 -62 4 0 0 1 54e. WPA2 CCMP PSK PALMER 94:F6:65:97:88:D8 -62 4 0 0 1 54e. WPA2 CCMP PSK Guest Wirele 94:F6:65:97:9E:88 -65 2 0 0 11 54e. WPA2 CCMP PSK Guest Wirele 94:F6:65:57:88:D8 -63 3 0 0 1 54e. WPA2 CCMP PSK AV Wireless 28:CF:E9:82:3D:52 -64 3 0 0 1 54e. WPA2 CCMP PSK Sierra 94:F6:65:D7:9E:88 -66 2 0 0 11 54e. WPA2 CCMP PSK PALMER 6C:70:9F:E5:0E:46 -66 2 0 0 6 54e WPA2 CCMP PSK WiFiFour 94:F6:65:57:9E:88 -67 2 0 0 11 54e. WPA2 CCMP PSK AV Wireless 94:F6:65:17:9E:88 -67 2 0 0 11 54e. WPA2 CCMP PSK Data Wireles 6E:46:0E:E5:9F:70 -68 6 0 0 6 54e WPA2 CCMP PSK Guest Networ Caught signal 14 (SIGALRM). Please contact the author! Caught signal 14 (SIGALRM). Please contact the author! root@Pineapple:/sd/captures#That's my capture in my pineapple. So yeah, I'm having a lot of problems. Could someone tell me how to fix that? Should I just move onto the next port scanner the book is trying to familiarize me with? This is done on my home network, with my working computer (which I call my school computer even though its a computer I personally bought and my school doesn't own it) as the target. In this case though, its the wifi that's the target, not the computer. In general, I think it makes a pretty good target.
-
I fixed it. First I fixed the Ethernet issue by using a program I downloaded called FixWin, the version for windows 10. I then applied all of the networking fixes and restarted my computer. Then, once Ethernet was working, I bridged the adapters and replicated the physical connection state and got it working even over wifi, as well as Ethernet.
-
I managed to fix it by resetting winsock and several networking related configurations using this program called FixWin for windows 10:
http://www.thewindowsclub.com/reset-tcp-ip-internet-protocol
After that, I restarted the computer and it let me log in with Windows. I can't get it to show up on Kali Linux 2.0 though but it let me get to the wifi pineapple management in windows at least. I need to get it to connect to ethernet in kali 2.0 and I'm good.
-
I ran this cmd:
Ipconfig /all >C:\pingresult.txt
and the ethernet section of this output is this:
Ethernet adapter Ethernet: Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Realtek PCIe FE Family Controller Physical Address. . . . . . . . . : 34-E6-D7-81-BE-DF DHCP Enabled. . . . . . . . . . . : Yes Autoconfiguration Enabled . . . . : Yes Link-local IPv6 Address . . . . . : fe80::b4e2:623:6404:61de%6(Preferred) Autoconfiguration IPv4 Address. . : 169.254.97.222(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.0.0 Default Gateway . . . . . . . . . : DHCPv6 IAID . . . . . . . . . . . : 406120151 DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-1E-10-EB-26-34-E6-D7-81-BE-DF DNS Servers . . . . . . . . . . . : fec0:0:0:ffff::1%1 fec0:0:0:ffff::2%1 fec0:0:0:ffff::3%1 NetBIOS over Tcpip. . . . . . . . : Enabled Ethernet adapter VMware Network Adapter VMnet1: Connection-specific DNS Suffix . : Description . . . . . . . . . . . : VMware Virtual Ethernet Adapter for VMnet1 Physical Address. . . . . . . . . : 00-50-56-C0-00-01 DHCP Enabled. . . . . . . . . . . : Yes Autoconfiguration Enabled . . . . : Yes Link-local IPv6 Address . . . . . : fe80::dcf5:8e1f:fb20:c7b2%4(Preferred) IPv4 Address. . . . . . . . . . . : 192.168.75.1(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Lease Obtained. . . . . . . . . . : Saturday, December 26, 2015 11:34:00 PM Lease Expires . . . . . . . . . . : Sunday, December 27, 2015 12:04:00 AM Default Gateway . . . . . . . . . : DHCP Server . . . . . . . . . . . : 192.168.75.254 DHCPv6 IAID . . . . . . . . . . . : 50352214 DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-1E-10-EB-26-34-E6-D7-81-BE-DF DNS Servers . . . . . . . . . . . : fec0:0:0:ffff::1%1 fec0:0:0:ffff::2%1 fec0:0:0:ffff::3%1 NetBIOS over Tcpip. . . . . . . . : Enabled Ethernet adapter VMware Network Adapter VMnet8: Connection-specific DNS Suffix . : Description . . . . . . . . . . . : VMware Virtual Ethernet Adapter for VMnet8 Physical Address. . . . . . . . . : 00-50-56-C0-00-08 DHCP Enabled. . . . . . . . . . . : Yes Autoconfiguration Enabled . . . . : Yes Link-local IPv6 Address . . . . . : fe80::ed8b:970b:dc4c:dfa9%13(Preferred) IPv4 Address. . . . . . . . . . . : 192.168.66.1(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Lease Obtained. . . . . . . . . . : Saturday, December 26, 2015 11:33:45 PM Lease Expires . . . . . . . . . . : Sunday, December 27, 2015 12:03:45 AM Default Gateway . . . . . . . . . : DHCP Server . . . . . . . . . . . : 192.168.66.254 DHCPv6 IAID . . . . . . . . . . . : 268456022 DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-1E-10-EB-26-34-E6-D7-81-BE-DF DNS Servers . . . . . . . . . . . : fec0:0:0:ffff::1%1 fec0:0:0:ffff::2%1 fec0:0:0:ffff::3%1 Primary WINS Server . . . . . . . : 192.168.66.2 NetBIOS over Tcpip. . . . . . . . : Enabled -
Yes, I ran it as administrator.
-
Thanks for telling me that. So then, I went to Geek Squad and they didn't even give me the Ethernet back. How sad? I need to take it in in person maybe and show them straight up what went wrong. If I reinstall windows 10, what does that do for me?
-
Umm, how are you powering it? Might need to reset it back to stock. Not sure what you want to do with a male male usb cable, but it's not going to do anything for you.
I thought the USB port in the pineapple could connect to the laptop instead of ethernet in the meantime.
-
I can't do any of this until I've solved these two issues, ethernet first, then the other one:
https://forums.hak5.org/index.php?/topic/37120-how-to-fix-ethernet-protocol-or-is-that-the-problem/
-
I also tried this in windows cmd prompt:
C:\WINDOWS\system32>netsh int ip reset resetlog.txt Resetting Interface, OK! Resetting Unicast Address, OK! Resetting Neighbor, OK! Resetting Path, OK! Resetting , failed. Access is denied. Resetting , OK! Restart the computer to complete this action.
Its like I don't have permission, just because of a basic refresh, to fix my own computer.
-
I was playing around trying to be able to connect to the wifi pineapple via wifi again, and I screwed up my ethernet by accident. The only adapter I can diagnose that has something wrong is ethernet. Here is my network adapters:
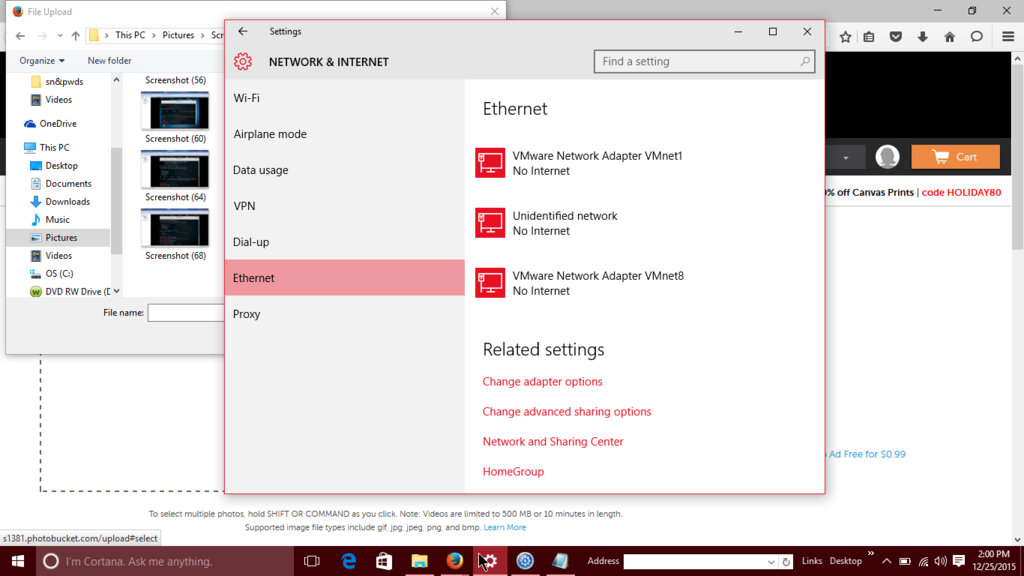
Here is the error I get when trying to diagnose it: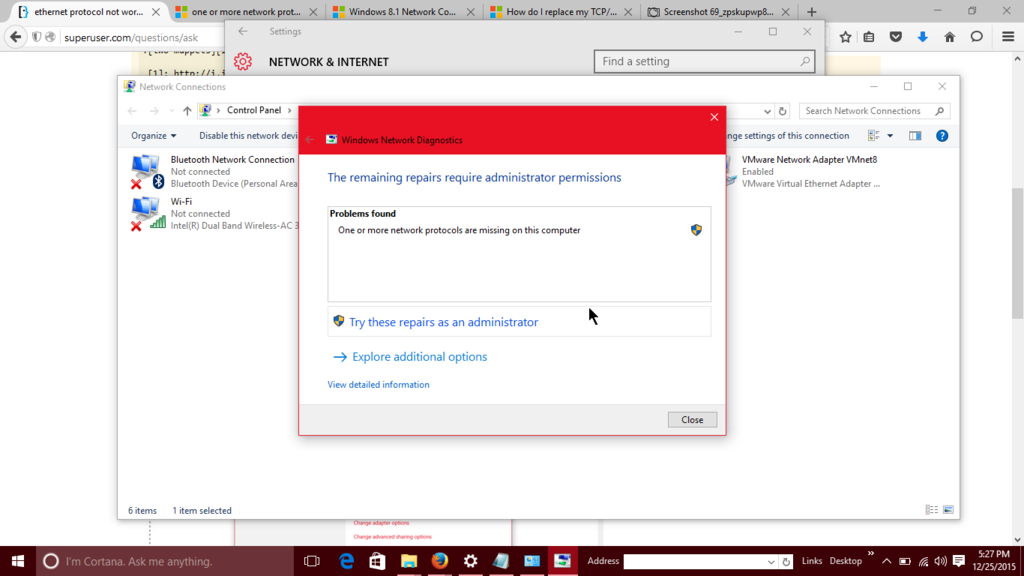
And when I try to fix it as an administrator: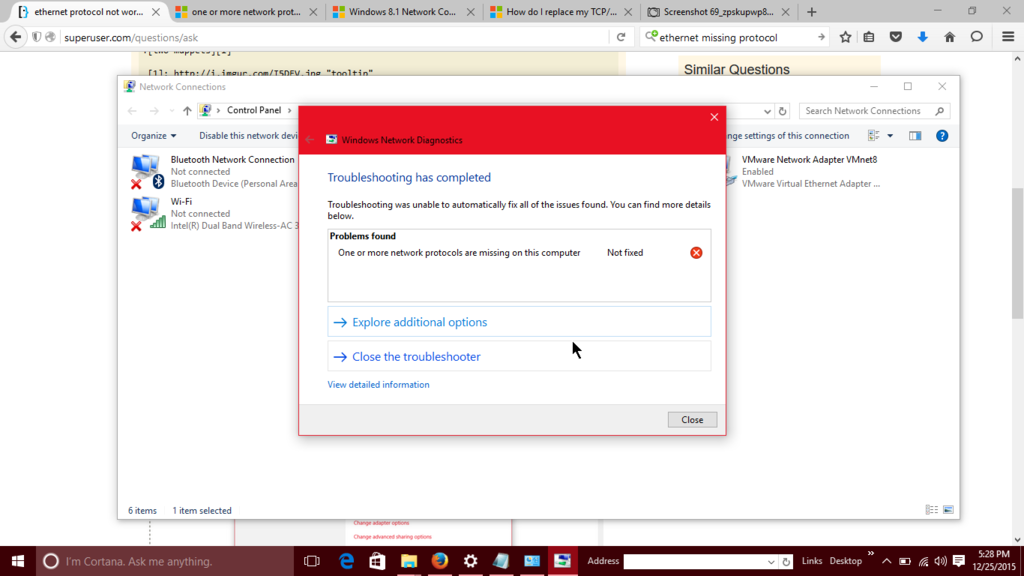
Does anyone know if THIS might work? I am scared of trying it:
https://support.microsoft.com/en-us/kb/299357
How do I get ethernet protocol again, or fix whatever the problem is?
-
I was playing around trying to be able to connect to the wifi pineapple via wifi again, and I screwed up my ethernet by accident. The only adapter I can diagnose that has something wrong is ethernet. Here is my network adapters:

Here is the error I get when trying to diagnose it:
And when I try to fix it as an administrator:
Does anyone know if THIS might work? I am scared of trying it:
https://support.microsoft.com/en-us/kb/299357
How do I get ethernet protocol again, or fix whatever the problem is?
-
I try typing in the ip address with the port, like 172.16.42.1:1471 and clicking enter until the cows come home and it never shows up anymore... At least, almost never. It hasn't shown up in the browser or wifi in several hours. I can't ping the device, even with the ethernet chord connected. I am wondering if a USB-Male-A to USB-A-Male would solve the problem or if I need to fix it over wifi. Ethernet light is on on the pineapple itself.
-
But I will try ssh into it first and see if it will let me then.
-
The Hacking Exposed Wireless Edition does for sure because I'm trying to do it right now. So then, I ssh into the pineapple. I'll do that. That was the command I tried when this command didn't work:
opkg --dest usb install tmux gpsd gpsd-clients
-
Also, it doesn't recognize the wifi pineapple ethernet cable. I don't have the SD card plugged into the computer, only the pineapple. lol. The output is:
root@blackJesus:~# opkg update && opkg install bash: opkg command not found
My pineapple won't connect in a way where I can use it on the cmd line is my guess. I can connect to it to configure it in the browser though. But that can't be enough to use it to learn wifi pen testing.
-
So, I want to install the USB packages:
root@pineapple:# opkg --dest usb install tmux gpsd gpsd-clients root@pineapple:# opkg install kernel kmod-usb-serial-pl2303
It gives me errors saying it doesn't recognize the command and can't locate the packages when I use "apt-get install".
I am a beginner at wireless hacking and I'm just starting to use the WiFi pineapple. It would also be nice if someone had read "Hacking Exposed: Wireless Edition", although not neccessary, since that's where I'm getting these instructions from. I'm trying to do this on kali linux 2.0



why won't kismet display MAC addresses?
in Security
Posted
Could someone please explain this?
I don't get why the names of the networks will all show up but not the MAC addresses. And why can't I scroll through kismet individually as opposed to the whole linux command line.