-
Posts
93 -
Joined
-
Last visited
-
Days Won
1
Posts posted by 3mrgnc3
-
-
Don't mind Cooper. He always has to give a contrary response in a thread. It's just how he wards of the script kiddie wannabes. He's doing the forum a service really.
Look, try not to take it personally, we have tried to give you the advice we think will best help you.
To be honest, if you aren't yet comfortable with Linux as your day to day pc I seriously recommend you make the switch to something like linux mint. Just by doing that and using it regularly you will become proficient in the basics as you encounter all of the small day to day intricacies of using a nix box.
It is entirely your choice friend, but I would make sure to do this before jumping into "Firing explots at boxes" and writing Ruby.
All the best.
-
I should have asked him about it all at DerbyCon. But I didn't want to interrupt his dinner on Sunday :P. He was just chillin in the hotel bar/restaurant.
?
-
Thanks for each of your responses. It gave me pause for thought.
You both have made very good points and I may have jumped to conclusions on this one.
Damn! I hate realising I'm doing that.
Cheers,
-
Another excellent resource is Vivek Ramachandra's securitytube.net site.
The megaprimers section is particularly good.
http://www.securitytube.net/groups?operation=view&groupId=10
But, as has been said. Grab something like linux mint, Debian 7, or one of the myriad other *nix distributions out there. And use it day to day. Play with bash to run stuff you normally use a gui for. Tinker and play and jump in the forums.
And do it because you love it.
Peace.
-
Aww man... before anyone says it. Yes I now see I missed the 'k' off the end of his name it the title of the thread.
-
I don't know about other people here, but back when I was starting out getting interested in security, Kevin Mitnik's books inspired me to believe in 'hacking' as a noble cause.
He compellingly made the case for following our curiosity towards the side of openness and fairness.
Ultimately we could use our passion for looking where the masses dare not, and make the future safer than yesterday.
....
But now I see my hacking hero of yesterday just wants to get paid today at the expense of tomorrow.
https://www.mitnicksecurity.com/shopping/absolute-zero-day-exploit-exchange
I guess the journo's nailed it a long time ago when they labeled him with the "Darkside Hacker" moniker.
I guess he just couldn't resist the emperor any longer.
-
Cheers guys,
Thanks for the info!
I'll probably try and get the StraightTalk deal while I'm over.
I'm gonna be staying just outside Baltimore, so I'll try and buy a sim in Washington When I fly in this weekend.
Thanks again.
-
So it's official! I'm finally travelling stateside for my company from the UK.
So I'm curious to know if anyone has any good recommendations for a reliable temporary PAYG SIM card I can use for the week in my Samsung Galaxy Note 3, while I'm working. Mostly I need one for data but I will probably be making half a dozen or so calls too.
I'm on a 4G SIM plan here that's faster than a lot of people's home broadband over the pond from what I gather.
I'm going to be in Maryland.
Anyway, any helpful advice would be much appreciated.
Cheers.
-
I have a question...
Does your kali system have to be connected to the pineapple? Reason I ask is because, correct me if i'm wrong, but the pineapple is on the 172. network, so how would the RHOST be anything different than the 172 network? In the example above, the kali machine is on a 10. network.
Does the pineapple send the shell or receive the shell?
Hi d0n350n,
The pineapple has multiple ip interfaces, and can be used in a variety of different configurations.
Try reading through this excellent set of guides from Scott Helme page:
https://scotthelme.co.uk/wifi-pineapple-mark-v-introduction-setup/
Also, I've found the info on Cisco's site helpful in the past.
http://www.cisco.com/en/US/docs/security/vpn5000/manager/reference/guide/appA.html
It should help you understand the main points.
Cheers.

-
Hi Seb,
Are you going to be upgrading the web config interface to https for the next fw release?
Well done and good work on everything so far btw.
cheers.

-
Mainstream Media... ha... :D
-
Your welcome feel free to give me a plus 1 ?
-
If this Troll is repeatedly going in and configuring mac filtering following each reset. I assume they are the only ones that have the administration password for some reason. Or, are able to break in each time themselves. (Following resets the default administration password is being changed to a complex one right?)
Failing the above, you could leave airodump-ng running on a device close to the AP on the same channel and with the bssid options set and write it to troll.cap. Then as soon as the filtering is re-enabled you should have captured whatever the troll does, and any other passwords they have used.
They it's just a case of looking through the file in wires hark to find the http login info for the Web interface of the router.
Peace.
-
I'm curious to know if Seb has any plans to include the harvesting of both BSSID's & corresponding ESSID's in order to be able to automatically spoof both together for a given target AP/AP's
I think this would be a useful counter measure against client devices that check for a matching sets of E/B SSID's before association to the AP's in its PNL. Although this isn't yet a common feature in most devices. I think this will become more of an issue in the future as more and more vendors play catch the mouse (or is that cat? Depending on your stance ?)
Also,
In the case of using multiple MKV's, in multiple locations on an engagement, the ability to remotely connect to a central file storage or database containing all harvested data would be very useful. Has this been thought of already anywhere else in the community?
Peace ?,
3mrgnc3.
-
Hey newbi3,
Did you manage to get this working at all?
I want to be able to do this to warn my friends and family when the 'End of Days' is really upon up and the Zombies rise up!
:D
Cheers,
3mrgnc3
-
very cool ;D
-
This sounds very useful for a phishing demo I'm planning ong doing for work.
I have to give some standard scripted infosec traing and I want to do something to grab the audience's attention. I will give this a try and let you know how it goes. Awsome work. ;)
-
Cheers.
I will try that. ;)
EDIT:
I tried it without any sleep or wait commands at the start of my boot script and it worked a treat!
Thanks again for all you tips. :D
-
You can add the following to your boot dip script:
/etc/init.d/autossh start >/dev/null &
Hmmn.. doesn't seem to be working as intended as a dip switch script.
I have experimented with adding a 3 min delay...
wait 180; /etc/init.d/autossh start >/dev/null &
I figured I would have to wait for my internet connection to be up before the command runs.
I can run your commands from the advanced tab in the webgui no problem.
should I just try a longer delay or is there a way to tell it only to run if an internet connection exists?
Thanks again for your help.

-
Cheers mate. +1 for you. I will give it a try tomorrow. ;DYou can add the following to your boot dip script:
/etc/init.d/autossh start >/dev/null &
-
Darren, is autossh supposed to autostart at boot by default once properly configured?
I have set it up and it works fine to my VPS if i manualy hit connect in the webgui.
Am I supposed to add a connect command to one of the dip switch config lines? If so what command should I use?
An option in the small tile to 'autostart at boot' would make this less confusing.
AWSOME work to the whole team on the MKV by the way.
Cheers. :D
-
Personally I suspect that DuckyScript hasn't been set up to handle key-triples yet, though I would be happy to be proven wrong.
Sadly I suspect that you may be correct there mate. :(
-
Have you tried CTRL-SHIFT ENTER instead of CONTROL-SHIFT ENTER?
Also what keyboard are you encoding for?
Have you had any error output whilst compiling the binary?
;)
-
Also, if you just want to see if the command works ok open the advanced tab in the web gui in execute 'iwconfig; iw reg set BZ; iwconfg' to see the the before and after effects to your tx power.
There isn't any real need to edit any of the default configuration prior to reboot.
the easiest way to manage this on the fly is to use the 'iw reg set' command for one of the dip switch configuration fields in the web gui.
e.g.
for people located in Belize!
iw reg set BZ
This if usefull if you know you are going to be pen testing in different regions and are required to ensure you comply with the local
regulatory domain requirements.
p.s
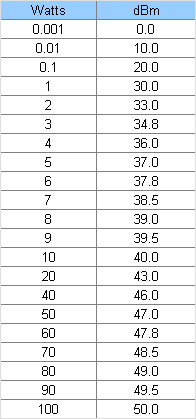
Belize allows tx power to be set @ 1 Watt (i.e. 30 dBm) and use of channels 1-13

Thank You mate ill give it a shot And let You know my results and I appreciate all the hard work you put in to research it



Total Newbs Seeking Help Cometh Ye Here
in Security
Posted
You're welcome.
And good luck mate
?