
MavproxyUser
-
Posts
65 -
Joined
-
Last visited
-
Days Won
1
Posts posted by MavproxyUser
-
-
-
None the less... some of you may be interested in my talk "KickStarting a Drone JailBrak Scene"
-
20 hours ago, C. Dave P said:
Shhhhhh, hear the crickets??
NONE of the original group hangs out here any more... we exclusively operate on Slack and GitHub now...
https://join.slack.com/t/dji-rev/shared_invite/MjIzMTI1MDA5MDcyLTE1MDIyMDgyNTItNzZkNTZhZjY4NQ
#DeejayeyeHackingClub information repos aka "The OG's" (Original Gangsters)
http://dji.retroroms.info/ - "Wiki"
https://github.com/fvantienen/dji_rev - This repository contains tools for reverse engineering DJI product firmware images.
https://github.com/Bin4ry/deejayeye-modder - APK "tweaks" for settings & "mods" for additional / altered functionality
https://github.com/hdnes/pyduml - Assistant-less firmware pushes and DUMLHacks referred to as DUMBHerring when used with "fireworks.tar" from RedHerring. DJI silently changes Assistant? great... we will just stop using it.
https://github.com/MAVProxyUser/P0VsRedHerring - RedHerring, aka "July 4th Independence Day exploit", "FTPD directory transversal 0day", etc. (Requires Assistant). We all needed a public root exploit... why not burn some 0day?
https://github.com/MAVProxyUser/dji_system.bin - Current Archive of dji_system.bin files that compose firmware updates referenced by MD5 sum. These can be used to upgrade and downgrade, and root your I2, P4, Mavic, Spark, Goggles, and Mavic RC to your hearts content. (Use with pyduml or DUMLDore)
https://github.com/MAVProxyUser/firm_cache - Extracted contents of dji_system.bin, in the future will be used to mix and match pieces of firmware for custom upgrade files. This repo was previously private... it is now open.
https://github.com/MAVProxyUser/DUMLrub - Ruby port of PyDUML, and firmware cherry picking tool. Allows rolling of custom firmware images.
https://github.com/jezzab/DUMLdore - Even windows users need some love, so DUMLDore was created to help archive, and flash dji_system.bin files on windows platforms.
https://github.com/MAVProxyUser/DJI_ftpd_aes_unscramble - DJI has modified the GPL Busybox ftpd on Mavic, Spark, & Inspire 2 to include AES scrambling of downloaded files... this tool will reverse the scrambling
https://github.com/darksimpson/jdjitools - Java DJI Tools, a collection of various tools/snippets tied in one CLI shell-like application.
-
8 hours ago, khaled said:
Hey can you please post a new Slack invite? the one in the OP no longer works.
Updated in original post...
https://join.slack.com/t/dji-rev/shared_invite/MjIzMTI1MDA5MDcyLTE1MDIyMDgyNTItNzZkNTZhZjY4NQ
-
19 hours ago, Slippy said:
I'm not sure but I would assume that any update after all this started a few weeks ago has the potential to block exploit.
several other exploits remain untouched.
-
 1
1
-
-
20 hours ago, Invernomuto said:
Is it true that the latest DJI spark update blocks Exploit?
It blocks one variant of RedHerring... by fixing the busybox tar dir traversal issue, and making /system "ro" instead of "rw"
-
I'll repost this here, as referenced in the dji_system.bin repo, this is a good place to start: http://dji.retroroms.infoFor those of you not in the loop, that want to help with the "retention" process regarding control of your DJI aircraft, please familiarize yourself with the following repos:
This represents the front lines of the resistance as it were... "the movement" pretty well begins in all of these individual battle grounds.

https://github.com/Bin4ry/deejayeye-modder - APK "tweaks" for settings & "mods" for additional / altered functionality
https://github.com/hdnes/pyduml - Assistant-less firmware pushes and DUMLHacks referred to as DUMBHerring when used with "fireworks.tar" from RedHerring. DJI silently changes Assistant? great... we will just stop using it.
https://github.com/MAVProxyUser/P0VsRedHerring - RedHerring, aka "July 4th Independence Day exploit", "FTPD directory transversal 0day", etc. (Requires Assistant). We all needed a *public* root exploit... why not burn some 0day?
https://github.com/MAVProxyUser/dji_system.bin - Current Archive of dji_system.bin files that compose firmware updates referenced by MD5 sum. These can be used to upgrade and downgrade, and root your I2, P4, Mavic, Spark, Goggles, and Mavic RC to your hearts content. (Use with pyduml or DUMLDore)
https://github.com/MAVProxyUser/firm_cache - Extracted contents of dji_system.bin, in the future will be used to mix and match pieces of firmware for custom upgrade files. This repo was previously private... it is now open.
https://github.com/jezzab/DUMLdore - Even windows users need some love, so DUMLDore was created to help archive, and flash dji_system.bin files on windows platforms.
So... that is all! Have fun folks, stop by Slack and see us if you get bored. #android_apk_patching, #archived_fw_flashing, #factory_mode_access, #firm_cache, #hardware, #mavic_rooting, #safety_shaming channels all have something for everyone. If not.. feel free to lurk in #general.
We are currently looking to archive as much firmware as possible if anyone wants to help... https://www.rcgroups.com/forums/showpost.php?p=37941901&postcount=1704
-
DUMLdore can be found here of course. You can use it to backup your DJI aircraft.
https://github.com/jezzab/DUMLdore
-
we have several firmwares backed up... we are looking for folks across various platforms to help us archive historic firmware using DUMLdore.
It would be nice if any of you Inspire2, or P4, P4+ owners could help us archive some of the historic firmware. Stop by slack in #archived_fw_flashing and ask how to use DUMLdore to get is dji_system.bin files for your specific version. You can of course go into Assistant and check your current version against the list below to see if it is something we are missing.
The current list is as follows:
MD5 (V01.00.0300_Spark_dji_system.bin) = bf81af1c10318e8549bb78b0fef85013
MD5 (V01.00.0330_I2_dji_system.bin) = 0a5c437812b91355c9ae0d4d28d505d1
MD5 (V01.00.0400_Spark_dji_system.bin) = 65f15f4cbe7d761459c7a09ebc660801
MD5 (V01.01.0010_I2_dji_system.bin) = 7d04f199bd872c9372fdebddbef3c404
MD5 (V01.02.0602_P4_dji_system.bin) = 36e11566ae6e303ec5c407f9c0f6c382
MD5 (V01.03.0400_Mavic_dji_system.bin) = a5ac037462b4f902bfa6cb8d9fe395ae
MD5 (V01.03.0400_RC_Mavic_dji_system.bin) = d5f40b9231786d6d5053539a78a105c5
MD5 (V01.03.0500_Mavic_dji_system.bin) = 2934111740e9cec3cd65029754b71fd8
MD5 (V01.03.0550_Mavic_dji_system.bin) = 34bdb52c8b8b7468f6312a5febf1838d
MD5 (V01.03.0550_RC_Mavic_dji_system.bin) = 06cc62f5d658c7461c758f3903b56c2a
MD5 (V01.03.0509_P4P_dji_system.bin) = 93a1663f6675a813ed494e260bb54e89
MD5 (V01.03.0600_Mavic_dji_system.bin) = f3a40d447c39bf8e946f2b5a087dccd6
MD5 (V01.03.0600_RC_Mavic_dji_system.bin) = 06b7657e1c8a42faf4b6f847eefcb438
MD5 (V01.03.0700_Goggles_dji_system-2.bin) = 76eefdb955bfa416e2f43f2ac9f86b84
MD5 (V01.03.0700_Goggles_dji_system.bin) = 47e7ea9eb5f5609bbd8141f7edb3516c
MD5 (V01.03.0700_Mavic_dji_system.bin) = 891904fad23add85e8c50a7902f272df
MD5 (V01.03.0700_RC_Mavic_dji_system.bin) = 8c11d7e04c03142a50cc0c9538d49fa6
MD5 (V01.03.0800_Goggles_dji_system.bin) = e2c93ded968c148f94c7a81776ce1dfd
MD5 (V01.03.0800_Mavic_dji_system.bin) = 6602c26ed0729581246853d7c988a4ae
MD5 (V01.03.0800_RC_Mavic_dji_system.bin) = e2508fbf87ce87c0dc7fb7721e555901
MD5 (V01.03.0900_Goggles_dji_system.bin) = 1f82d27681217b4c388a593e4ba6f875
MD5 (V01.03.0900_Mavic_dji_system.bin) = 984446beb028443670091e07d3bbd752
MD5 (V01.03.0900_RC_Mavic_dji_system.bin) = beb6c9dea2a0ad5f688ada4d439e969f
MD5 (V01.04.0602_P4P_dji_system.bin) = 2a6b5baba26aa3203ecdc5450ba0473f
MD5 (V02.00.0106_P4_dji_system.bin) = a49944bb254354ec064bee13c491fa1eFor those of you that can already use git, and have no problem figuring out DUMLDore just submit us a pull request similar to this:
https://github.com/MAVProxyUser/dji_system.bin/pull/6/files -
Current pyduml:
https://github.com/hdnes/pyduml/commit/b7636619371462cf62f12b98e456e5a2f68e1b99
Current *combined* root/.400 Mavic downgrade.
(this is no longer a private Git account... anyone can access it)
https://github.com/MAVProxyUser/dji_system.bin/commit/c32b67c9853a195e4c8bfbf9a6e357c777675250$ python pyduml.py /dev/tty.usbmodemXX
55 16 04 FC 2A 28 65 57 40 00 07 00 00 00 00 00 00 00 00 00 27 D3
55 0E 04 66 2A 28 68 57 40 00 0C 00 88 20
55 1A 04 B1 2A 28 6B 57 40 00 08 00 00 18 54 07 00 00 00 00 00 00 02 04 94 0B
55 1E 04 8A 2A 28 F6 57 40 00 0A 00 86 B3 22 02 66 12 E9 6F A0 93 73 BC 85 60 67 4A 6E 18
Firmware Upload Complete
(wait 5 minutes, like for real!)# telnet 192.168.42.2 1234
Trying 192.168.42.2...
Connected to 192.168.42.2.
Escape character is '^]'.
id;
uid=0(root) gid=0(root)for ADB access...
rm /data/.bin/grep; (via telnet)sh-3.2# adb devices
List of devices attached
RedHerringHasFangs devicesh-3.2# adb shell
root@wm220_dz_ap0002_v1:/ #To make your own:$ cp UniversalFireworksTar_dji_system.bin mavic_combined_400_root.bin
$ gtar --concatenate --file mavic_combined_400_root.tar V01.03.0700_Mavic_dji_system.bin
$ tar tvf mavic_combined_400_root.tar
-
Current pyduml:
https://github.com/hdnes/pyduml/commit/b7636619371462cf62f12b98e456e5a2f68e1b99
Current *combined* root/.400 Mavic downgrade.
(you can't see this unless you give me your GitHub name via slack)
https://github.com/MAVProxyUser/dji_system.bin/commit/c32b67c9853a195e4c8bfbf9a6e357c777675250$ python pyduml.py /dev/tty.usbmodemXX
55 16 04 FC 2A 28 65 57 40 00 07 00 00 00 00 00 00 00 00 00 27 D3
55 0E 04 66 2A 28 68 57 40 00 0C 00 88 20
55 1A 04 B1 2A 28 6B 57 40 00 08 00 00 18 54 07 00 00 00 00 00 00 02 04 94 0B
55 1E 04 8A 2A 28 F6 57 40 00 0A 00 86 B3 22 02 66 12 E9 6F A0 93 73 BC 85 60 67 4A 6E 18
Firmware Upload Complete
(wait 5 minutes, like for real!)# telnet 192.168.42.2 1234
Trying 192.168.42.2...
Connected to 192.168.42.2.
Escape character is '^]'.
id;
uid=0(root) gid=0(root)for ADB access...
rm /data/.bin/grep; (via telnet)sh-3.2# adb devices
List of devices attached
RedHerringHasFangs devicesh-3.2# adb shell
root@wm220_dz_ap0002_v1:/ #To make your own:$ cp UniversalFireworksTar_dji_system.bin mavic_combined_400_root.bin
$ gtar --concatenate --file mavic_combined_400_root.tar V01.03.0700_Mavic_dji_system.bin
$ tar tvf mavic_combined_400_root.tar
-
 1
1
-
-
They are sent via FTP ...
You can catch via ADB (with existing root access)
adb pull /data/dji_system.bin
or
Via cp (with existing root access) (and copy to a spot you control and can get to later)
while true ; do cp /data/dji_system.bin /data/xxx.bin; done
-
Game over...
Confirmed ability to downgrade firmware to any version you have the .bin for.
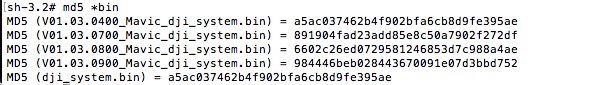

-
3 hours ago, spamsuxx said:
Hej all,
I am on .700 and the patched DJI Go 4.1.3 Android app and it show "Cannot take off. Aircraft locked. Update to the latest version."
I think at some point, before I manually install the patched DJI Go 4.1.3 app, the updated DJI Go app locked the Mavic (couple of days ago).
I hoped that downgrading to the patched DJI Go 4.1.3v6 fixed the lock, but it didn't.
So, did DJI set a flag in the Drones software itself or is there a remnant on my phone which prevents the Mavic from take off?
Any suggestions are welcome.
Cheers!Stop on by the slack mentioned in the first post... very few folks are on this thread these days... but slack is on and poppin.


-
I know a lot of Windows users have wanted to play... as of This commit I believe you guys are good to go. Let me know of any bugs please.
https://github.com/MAVProxyUser/P0VsRedHerring/commit/ac04a117cbea49dfcfecd216b2ed62d751cd03dd
-
30 minutes ago, techspy said:
Does having root get us any closer to using the FW dumps located here? And, will it allow us to modify these dumps and for example remove the NFZ from 800/900?
short answer... yes. There is a HUGE hint to this in my *original* post in one of the statements I made, and photos I added (inside IDA pro).
-
*confirmed* we just rooted Mavic, and Inspire2 with RedHerring. - https://github.com/MAVProxyUser/P0VsRedHerring/commit/94e6f2c098a1c8556320d0ee994f3b6fa3e1ff03 Phantom4 series, Mavic Pro, Inspire 2, and Spark #Jailbreak
-
-
-
You folks messing with exceeding max limits... So the max 2500 must be .400 specific? See notes at https://aeon7me.wordpress.com
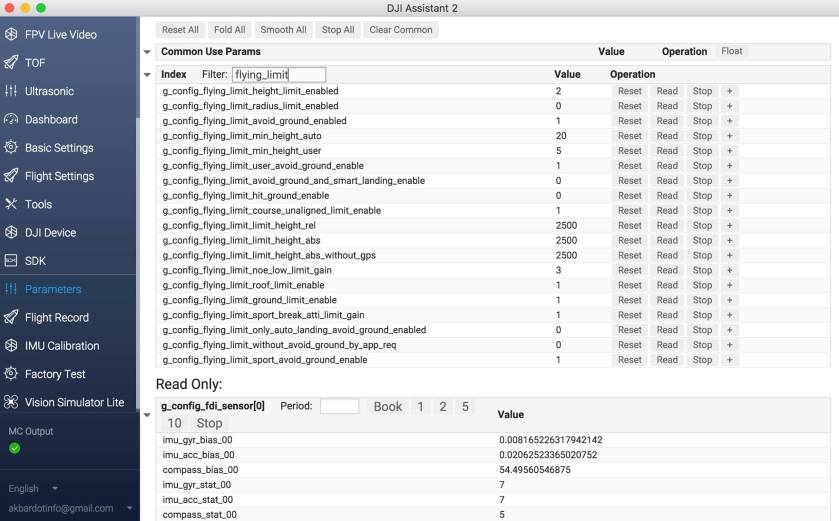
-
5 minutes ago, singlag said:
found something about ce/fcc switching, this method is from dji china forum, i try to translate to english here
It is depend on dji go app
how it work:
dji go app will first get location from data network, if no data network, then it will get from sim card carrier/operator; if no data network and no sim card, then set to CE as default
so, you can fake it by a android with root
1) clean install, remove all cache from dji go app (not sure is it necessary)
2) disconnect from data network
3) use app to fake country operater code to US
http://androidadvices.com/fake-country-operator-carrier-download-paid-android-apps/
4) start dji go app
how to check result ?
the only version can check is 4.0.6
go to setting, keep click on "Flight Controller SN", then it will pop up a secret menu and show country code
actually there is a password to change code manually, and also device SN !
but he don't share the password because it is too danger to share to public (but I guess we can change SN by web socket command ?)
attached secret menu creenshot found on my phone
nice work thanks for sharing.
-
This Google Spreadsheet was shared and it was suggested that we should begin archiving known good settings and what they do here:
https://docs.google.com/spreadsheets/d/1X0MAgELkSQBb0GCfhP6gLfQa0rfW1T5GtYRGilBIozg/edit#gid=0
-
1 hour ago, mavicBreak said:
What is the reason? All firmware files from 200 to 900 are already available in a github repo.
For one Github is known to comply with requests to takedown content if copyright holder asks. Secondarily... I just wasn't aware of said repo. =] The more mirrors the better at this point. Also keep in mind there are 4 different aircraft Spark, Mavic, Inspire2 and Phantom4. I don't believe *all* have been archived. Never mind the A3, and other devices assistant supports.
-
10 hours ago, enderffx said:
Do you have any idea if that version supports Spark as well ? If not then all this probably is irrelevant for Spark, right ?
---Trying to get a grip on this, but just beeing a regular coder and not well versed on hacking / rev engeneering its hard for me---
Ender
I've successfully tested all of this on Spark. It is all applicable for the following models Spark, Mavic, P4, Inspire2





MavicPilots.com Alternative CopterSafe Hack & Mod Discussion
in Community Projects
Posted
It is about that time for everyone to email all of the following email addresses and ask "WHERE IS MY OPEN SOURCE!?" opensource <opensource@dji.com>, "adam.lisberg" <adam.lisberg@dji.com>, "Yin.Cheung" <Yin.Cheung@dji.com>, Logan Wang <xiaodan.wang@dji.com>, "Ted.Liu(刘岿然)" <ted.liu@dji.com>, Owen <cheng.ouyang@dji.com>, "Brendan.Schulman" <Brendan.Schulman@dji.com>, "jon.resnick" <jon.resnick@dji.com>,