
decepticon_eazy_e
-
Posts
164 -
Joined
-
Last visited
Posts posted by decepticon_eazy_e
-
-
Anyone know of any? The smaller the better.
ITX is what you want if you want small.
They have everything you'll need for a tiny PC, I've ordered from them, pretty easy to work with, no probs.
-
I'm doing this to my own house as well. I looked the cost difference and a spool of CAT6a is not much more, so that's what I'm doing. In 10+ years I'll be happy that I did.
I'm also running the coax and phones, most phone cable is now cat5 so it's all the same now-a-days. My builder is only giving me a couple hundred as credit for doing it myself, but that's only covering the 4 or so outlets he planned on. I plan on 2+ per room, 4 in the living room and family room.
I think it's a great idea, do it right and overkill the first time, and it will last for years! Not to mention the nerd cred you get for a project like this! :)
-
Spoofing an IP and using a VPN will never mix. The IP address is typically rolled into the certificate exchange during the VPN (IKE handshake) setup. So you need to be the IP address that you are advertising you are. It also makes a difference if we're talking split tunnel vs full tunnel.
VPN behind a NAT router works because there is a 1 to 1 translation. Dynamic NAT and VPN only works up to a point, GRE is on port 0, so only 1 person at a time can use a GRE tunnel run behind a dynamic NAT router.
We can get this more complicated if you want. :)
If your server is one of those IP addresses that is not dynamic and is reachable, you can get to it. Install OpenVPN, google for a tutorial and go. It'll work fine. You can browse that network because your server will NAT you to it's own IP (in a full tunnel mode). You won't be browsing that network if you use split tunnel.
If you think all this is too complicated to get going, install Hamachi on the server and your other PCs and call it day. Should take about 15 mins to finish that project.
-
And wouldnt mac addresses cause this to be IMPOSSIBLE? otherwise routers with "default" for names and such would be rampant random connections, a fair percentage dont change default names either outta laziness or unknown knowledge of how to.
just my 2 cents
XP has this fixed now, so you don't connect to random connections, even with the same SSID. But up until then, nope, that is exactly how it worked. That's what the whole "evil twin" attack is based on.
Same with the pineapple/jaseger thing. The only difference there is that it's waiting for your card to look for old SSIDs. You still connect to an AP with a SSID that's a spoof of one you've been on.
Companies sell expensive WLAN/IDS devices/solutions to counter act the whole "rouge AP" problem, which is exactly what you're talking about.
So, it's far from IMPOSSIBLE, it's more like COMMON EVERYDAY PROBLEM WE DEAL WITH.
-
Yeh I did spend like $150 on a Logitech wireless keyboard and mouse but remote desktop is just easier
 .
.Random pic at work I found lying about...

Our patch panel is an extreme spaghetti board... and its only going to get work with renovations all over the office
 .
.2 cisco 7206VXR chassis with NPE-G1 or G2s, just above 3 WS-C3524-XL-ENs. Next to it is a 4507 chassis with dual sups (sup2?), below are more 3524s.
Pretty good redundant setup!
-
So since the WLAN is not allowing me to go outside as per the ACL's there is no way out to the outside world ?
Yea as you said I think everything is blocked so I don't see a way out. But I was wondering DNS should have a way out.
On that note does anyone have a full fledged article or something on DNS where in I can read the ins and outs of it. Detailing every aspect of it. Let me know if anyone in the community knows.. Thanks for the help so far.
Why do you think DNS is open? You said before when you do an nslookup it comes back with nothing. DNS probably is open in the VPN'd subnet, not the one you are in.
-
hahahah thanks for the warning... I know what you mean ... but I just have to try it .... I am too freaking curious to know what their setup is and how the hell they are blocking it.... thats just me
and as what you said I did try that....
tell me tell you how the setup is ...
When I connect to the access point
the IP I am assigned is 192.168.218.*
the gateway is 192.168.216.1
the DHCP server is a different ip 134.88.3.*
and the Dns server is 134.88.1.*
So as you said I changed the dns server to the gateway and then to the dhcp address respectively
but it still wont freaking resolve anything....
What's your mask? if it's /24, your gateway is in a different subnet.
I assume their network is setup like this... 192.168.218.x is the WLAN. Those people need to VPN into another subnet, such as 192.168.216.x The 216 subnet has an ACL that allows it out to the internet. The 218 subnet has an ACL that does not. No amount of tunneling will work as long as your IP address is in the 218 range and you are on that WLAN interface.
Tunneling is for when ports are filtered. From what you are saying, I don't think that's your problem.
-
It will run. I worry about running a firewall as an application though, cause really that's what it becomes when running in a vm. In my opinion it would be better to just pick up an older low power laptop, or mini-itx machine to run the firewall as a dedicated box.
http://www.vmware.com/appliances/directory/47
Yup, they already did all the work for you.
-
OK, Thanks for the reply Decepticon,
...
so by using the deployment diagram that i supplied on top, it is not possible to achieve high performance greater than single cable connection :-|
hope that helps you in the future,
Cheers,
Devastated and desperate admin :-(
Exactly right, NIC teaming and link aggregation are for failover purposes more than throughput. However, what I had in mind is what will happen when you add a second VM on the same line. If you bundle up your NICs onto a single virtual switch, the next VM will get a different NIC. By default it's round robin allocation, so the second VM will get the second NIC in line. If they all shared the same NIC, I assume the throughput goes down dramatically.
Also, you mentioned not having a switch with VLAN capabilities. A better switch will have better processing power and thus faster throughput. I assume you are not running this test through some Netgear switch from Best Buy. A better switch will have better results.
-
Hi Decepticon,
I was thinking to redesign the network all over again from scratch,
instead of having different subnet for each cable and then perform LAN
teaming so that 2x 1 GB Ethernet cable can boost the data performance
for the VM without the use of any switch in between the SAN and Servers.
well, the case is that:
in total 15 x 300 GB SAS HDD
I've created large RAID-5 LUN from 14 x 300 GB and then i created 1 TB of
VMFS partition and the SQLIO benchmark is really horrible for the VM on
the SAN as oppose to the local SATA 7200k rpm.
see the result below:
*Local HDD: 4x 500 GB SATA 7200 rpm RAID - 5 *
C:\SQLTEST>sqlio.exe
sqlio v1.5.SG
1 thread reading for 30 secs from file testfile.dat
using 2KB IOs over 128KB stripes with 64 IOs per run
initialization done
CUMULATIVE DATA:
throughput metrics:
IOs/sec: 8826.73
_MBs/sec: 17.23 _
while
*SAN HDD: 14x 300 GB SAS 15000 rpm RAID - 5 *
C:\SQLTEST>sqlio.exe
sqlio v1.5.SG
1 thread reading for 30 secs from file testfile.dat
using 2KB IOs over 128KB stripes with 64 IOs per run
initialization done
CUMULATIVE DATA:
throughput metrics:
IOs/sec: 2314.03
*MBs/sec: 4.51 *
Interesting results! I would assume the difference is the processing done to iSCSI on the kernel. There's extra overhead on the CPU and OS (ESX) when iSCSI is used with no iSCSI hardware initiator. It's doing a software conversion from disk I/Os to IP packets, but I didn't think it would be so apparent.
If you could get ahold of an iSCSI card and put that in, I'd love to see the same test done and see how much that changes things. QLE4050C is the most popular/common one I see at work.
What do you get for CPU utilization during these tests?
-
Pretty sure it's the router and not a problem with software. I guess the kernel module doesn't know how to handle whatever kind of packets the router was tossing out. It causes the entire LAN to go down. No wi-fi either. I have two wireshark files here, one of just the network idling (supposedly) which contains an interesting little destination unreachable (host administratively prohibited) that is not in my /etc/hosts.deny file.
This some of these, like the first 3, are repeated.
The nmap wireshark seems fine..... no lost packets.
Destination unreachable is an ICMP code, not something generated that is actually being blocked by your host file.
It means that somewhere in the chain a router decided it didn't have a route for that network, or that network is denied for some reason. So the packet is actually going out and somewhere it gets a message back that it's denied. That IP is owned by the internet people, ARIN? That's a weird one. Maybe they're detecting the scan and sending custom packets back. Who knows!
-
Here is my beginning diagram.
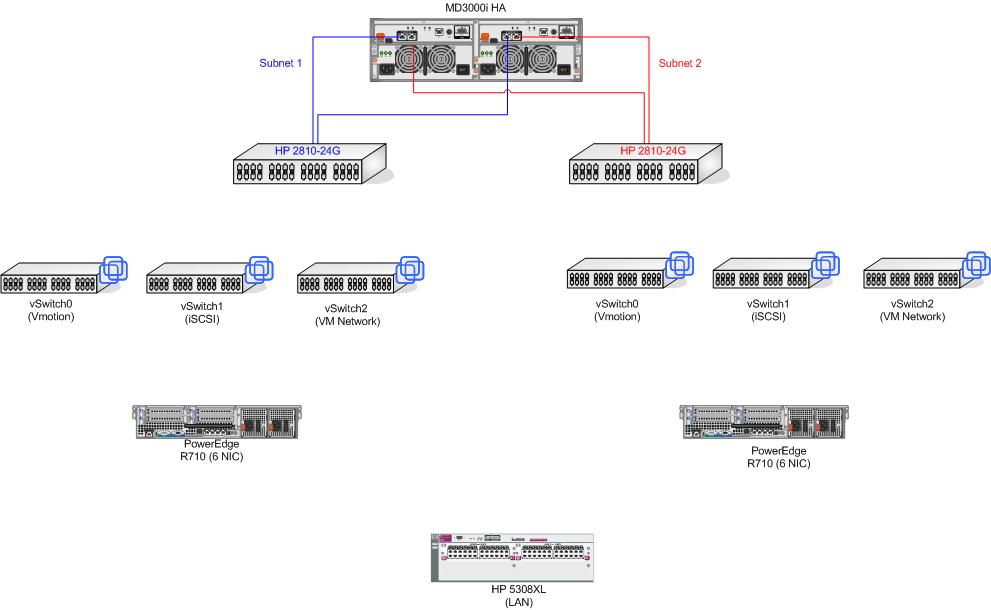
Ok, that's a good start.
I would recommend a minimum 6 ports per server with that setup. 2 for each of those "networks". Now take those 2 ports for each of those "networks" and put them on different modules on the core switch. This gives you a failover option on each network, and on the physical switch. The modules can be swapped out if they fail. Pick modules on separate backplanes (left and right) and you get get failover from the backplane.
This is all best practice according to VMware, but I'll throw out a different solution. Take the same 6 ports on each server, join them to the same vSwitch and use port groups on the vSwitch to divide up the "networks". Now instead of 2 physical ports for failover, you have 6. Meaning 5 physical ports on the server, or on the switch, can fail before you have an outage on the server. Much better, yes?
Those ports on the switch need to be trunks, with a vlan for each of the "networks". The SAN would reside in your iSCSI vlan and nothing but those trunk ports from the servers will exist in your vMotion vlan. The vMotion "network" will get it's own range of IPs, which is trivial, but there is no default gateway set. That ensures that traffic can't get in or out from that subnet/vlan/"network".
I assume there's some kind of management port on the SAN, if that's rolled up on the same ports, you'll have to figure out the trunking protocol there. I guarantee there will be some solution provided by the SAN manufacturer for this.
Your production "network" will be vlan 1, since that's what you started with already. You're iSCSI and vMotion will something else between 2 and 4000-something.
If you have the ports available, I recommend you put the SAN and the servers on the core switch. It's your fastest and most resilient switch with the best failover options. Either way put the SAN and the servers on the same switch, eliminate as much lag as possible.
Research "vlan hopping" to explain why you should never use vlan 1 in your production network.
-
Hi All,
I'm suffering very slow performance in using my VM deployed on the iSCSI SAN-VMFS datastore, the following attachment shows the deployment diagram which i believe already according to the best practice around the net by segregating the network from SAN into the server.
http://virtualgeek.typepad.com/virtual_geek/2009/01/a-multivendor-post-to-help-our-mutual-iscsi-customers-using-vmware.html
However, after reading the quoted article, it seems that no matter how fast the disk is, using SAN
in a VMWare environment it will always be slow around 160 MBps :-|
This usually means that customers find
that for a single iSCSI target (and however many LUNs that may be
behind that target 1 or more), they can't drive more than 120-160MBps.
is there anything that i should do to boost performance ?
Thanks.
--------------------------------------------------------------------------------------------------------------------------------------
FYI: This is a continuation from this thread:
You are quoting mega BYTES of data. 160 mega BYTES is the equivalent of 1280 mega BITS per second. That comes out to approximately 1.2 gigabits per second. We all know it's almost impossible to get a full gigabit of throughput on a gigabit switch (overhead, packet drops, etc), so I'd say that's pretty good. They used link aggregation to get that 1.2gbps of throughput to the disks, so that's how it's over 1gbps.
You'll never get that high on fibre channel (nothing close to link aggregation or etherchannel), so I'd say that example just showed iSCSI as a faster solution.
-
- At the console press Alt-F1
- Then type "UNSUPPORTED" and press <enter>
- Login with your root login and password
If you just want to virtualize windows then Hyper-V from micrsoft (a free download and part of with Server 2008). Its far less restrictive when it comes to hardware, but a less mature product. I've set it up on a laptop before and it worked ok. Linux can run under Hyper-V but it will be a bit more hit and miss.
There is also Xen, Citrix and Parallels you can look at, but I have no expirence with those products.
He's using 3.5, so no need for the "unsupported" stuff, this one has the full CLI. Check the VMware HAL to make sure your NICs are supported.
Use some of these commands in ESX 3.5 to troubleshoot your NICs.
esxcfg-nics –l
Display physical NIC configuration
esxcfg-vswitch –l
Display virtual switch configuration
esxcfg-vmknic –l
Display VMkernel ports
esxcfg-vswif –l
Display service console interfaces
-
VLAN 1 is the production VLAN. Isn't that the default setting? This network was already in place when I was hired, and only had the default VLAN. Does it really matter that VLAN 1 is the production VLAN?
VLAN 1 is always the default setting on every switch, which is exactly why you shouldn't use on any of your switches.
-
I was under the impression that different subnets could be used, rather than VLANs - am I wrong or do you have to do both?
Well I like the idea of putting the iSCSI traffic on a different switch/switches. All of the switches in my network are HP, maybe a couple 24 port 2810's would work. At this point I'm confused as to how the VM's will be visible to my LAN.
subnets and vlans usually correspond, but they don't always have to. Best practices usually dictate no overlapping subnets, i.e. each subnet belongs to a specific vlan. But I already said the thing about best practices...
You can have as many subnets in a single vlan as you want, nothing will prevent you from configuring it that way. The problem lies in having broadcasts that belong to subnet X overlapping with subnet Y. For example 10.10.10.10 is an address in subnet 10.x.x.x, but also in subnet 10.10.10.x, so what broadcasts should it respond to? VLANs will segregate those broadcasts (which is why they call it a broadcast domain) from each other, and mitigate that specific problem. It's up to you to plan it out correctly and avoid such problems. Putting iSCSI in a closed dedicated vlan makes sure that traffic is not overlapping or interfered with from another subnet or vlan. I explained that more thoroughly in another thread.
The VMs that will be visible to your network are up to you, your LAN has a vlan, put the VMs in that same vlan and there you go. I will assume you planned ahead and didn't make VLAN 1 your production vlan.....
If you are confused by all this, put all into a diagram and map it out specifically. If you plan it right, you can implement it right. If you plan it wrong, you can never implement it right.
-
I'm still kind of fuzzy on the whole Portgroup thing, but I'm getting there.
Each vSwitch will assign a VLan tag. The corresponding ports on the 5308XL will allow that VLAN traffic. Is that correct? If so, I don't understand what happens to the traffic after that - how does it get to the SAN?
Traffic gets to and from the SAN via VLANs, you need to configure them properly on the switch and the SAN as well as the ESX servers. I recommend you study up on those and figure out how to VLAN on a procurve as well as the SAN before you implement.
I think there is a bit of confusion about the core switch. I already have the 5308XL; it just doesn't have a copper gigabit module in it yet. It is currently the core for my network (fiber modules connect campuses/buildings), and I'm not sure if putting a gig copper module in it for the ESXi servers/SAN is the right way to go about this project. Maybe getting a new separate gig switch would be better? I would only be putting in 1 14 copper port module, would that even be enough? If each server has 6 NIC ports, that would eat up 12 right there. I might need two modules...Ok, I didn't realize you had the switch already. You need to decide if having the server and SAN traffic on the core is right for you. We can't see where your data goes, so we can't say. If all the data on those servers hits the core and needs to be gigabit, then I would say yes, put it on the core. If you have a majority of traffic that is server to server, or doesn't need to be delivered at top speed, then maybe off load to another switch.
Our typical configuration/recommendation is 2+ cisco 3750s stacked. You then spread your NIC connections over the 2 or more switches for failover. Everything has at least 2 paths to everything else, you have a pretty safe setup that way. HP has options similar to that.
Also, I would never recommend a direct attached solution when you have a SAN. You bought a SAN with redundant iSCSI controllers for a reason. If you directly attach them to the server, you should have bought a JBOD and saved money. You will have to completely rebuild your setup if you want to add a 3rd server down the road. Always plan for expansion and you will never out grow your hardware.
-
I would guess that you are DoS'ing your own router/modem. There's a finite amount of ram in those devices to hold open connections, if you do a big enough Nmap scan you're probably filling that up too fast.
Narrow your scan a bit. I use (on a windows box) angry IP scanner to get live or "up" ip addresses quickly in a given range and then use that list to scan ports on, instead of just doing a full port scan on thousands of addresses at a time.
-
Alright, let's go through this one at a time.
Hello all - I am the network admin for a public school. I'm going virtual with my servers, and could use some help - especially with the LAN configuration. I am getting 2 servers (Dell R710, dual Xeon 5520's, and 48gb ram) and an MD3000i SAN (15 146gb 15k rpm SAS drives). VMWare Infrastructure Enterprise edition, Virtual Center Foundation.
Pefect, that's a good start.
I don't have a gigabit switch, but plan on getting a gigabit copper module for my HP Procurve 5308XL. That switch is the core switch for the entire district.
Good, those are nice switches. You won't be doing much here until you get that switch though...
Would putting that module in the 5308XL and using it for iSCSI connections be OK? I know you should have 2 switches for redundancy, but I figure if the core switch goes down, everything goes down regardless. If that would be ok, do all of the iSCSI connections need to be on a separate subnet and have a vswitch handle VLANS? Or are the VLANS handled by the 5308XL?
Yes, iSCSI runs just fine on that. iSCSI should sit on a dedicated VLAN, that's correct. The vswitch does not create vlans, at all. It tags packets on the way out of the physical box that correspond to whatever vlan you assigned it. So the port directly attached should be a trunk, with the appropriate vlans allowed.
Redundancy. You are getting a switch with redundant power supplies and hot swap modules. So you have the equivalent of multiple stand alone switches, take advantage of that. The diagram Matt did in the last episode that showed all the switches separated and isolated is only best practices. Best practice and real world possibilities only meet on Sundays for church, they rarely work together. Lump as many of the ports you have on each server together on the vswitch. You will have the most failover that way. Put them all on as trunks on the HP switch. Spread the ports over as many modules as you can. That way if one backplane goes down, or module or supervisor engine goes down, the server will stay up. Do the same on the other server and the SAN, you should have a pretty bullet proof system.
As none of the equipment is ordered, you should add as many gigabit NICs to the servers as possible. If you feel that read/write disk access will be your bottle neck, swap out a NIC for an iSCSI TOE card. Check the VMware HAL before you order. I can't make that call for you since I don't know what will be running on there.
Swap out all of the modules in the 5308 for gigabit, there's no reason not to. Your core switch should not be 10/100.
-
Go on some career sites and look for jobs you might want. See what they ask for in certifications, it all depends on what you want to do. For example, I do NOT want to spend my day troubleshooting IIS and Exchange, so I won't be getting a cert that reflects those skills.
Figure out what you want to do rather than what you think will pay the best, if you are good at ANYTHING, you can make money at.
-
-
Fixed.
Do you speak German or Russian? Oh, oh, maybe you speak French or Spanish?
However, when you at least try to speak or even to understand my own language, then come and tell me if I broke the laws of English.
I'm not ashamed writing with your own language because I'm sure if I started to write in my own language you wouldn't understand a word.
Fixed. It has nothing to do with foreign languages, it's proper grammar. When you speak on a forum like this, we only see how you type and what you type. We have no other means of judgment beyond that. This is why you get judged the way you do. The little red underlines are there for your benefit and the benefit of others. Those special dots and lines are for ending sentences, not just making funny emoticons. I'm sorry to rant like this completely off topic, but it drives me nuts when somebody comes on with a post like that and then gets upset when people criticize him for it. This is not a text message on your cell phone, take the time to proof read your post if you want to be taken seriously. It's a good habit to get into before you enter into the job market. You mention you are in college, I have a hard time believing you get to write like that for assignments.
I'm sure I'll get flamed for this, but I'm just going to say what everyone else who read your post is screaming in their heads!
-
You have broken the law... regardless of intent.
He has also broken the laws of English. That's got to be one of the most difficult posts to read ever posted here.
Has anyone really been far even as decided to use even go want to do look more like?
-
**double post***
ok, so I do have one port that it nmap questions as a jetdirect port.
Seemingly enough, the only info I could find for lexmark is this port is used to send raw doc's that up copy to the ftp server, it prints the docs and then deletes it off the ftp...
Linux printing for lexmark anyone? (pffft. finally....)
Ok, so Net tools simple fast port scanner found more ports?!
80
110 *pop
119 *Network News Transfer Protocol
143 *Internet Message Access Protocol
8000
9100
10000
nmap came up with 80, 8000,9100, and 10000, but the rest? hmmm...
so 110 is for pop? this is rather odd. maybe something special in the software though.
I think it's time to put a sniffer on that and see if those ports get used, and where they go. Maybe it calls home?

DEFCON - Hacking Conference
in Everything Else
Posted
You can't pre-register, you can go the night before to get your pass, avoid the lines (HIGHLY recommended). Last year they ran out of the cool badges and handed out laminates instead, lame. Go early!! CASH only, I don't recommend using an ATM there, they're not safe.... ;)
I went the last 2 years, it's so worth it! If you look at the price of other similar cons, this one is so much cheaper too.
To answer another thread, yes vegas has no laws about open containers. You can take your beverage from the liquor store or bar and walk around with it and go into other bars and casinos. Nobody hassles you about that stuff.