-
Posts
106 -
Joined
-
Last visited
-
Days Won
3
Posts posted by Fallen Archangel
-
-
Hello
I'm known as the local "tech kid" around the neighborhood, and I've been asked to do some stuff at a high school graduation later today. I brought up the same thing that that was done here, and know I'm trying to think of good SSIDs to broadcast. Any ideas? Thank you.
-
At the thirty second mark of "Tiny Hardware Firewall Review"
-
My first guess is that the use of MD5 is deprecated pretty much everywhere by now. Chances are the Nano is rejecting the attempt due to insufficiently strong crypto. Look in the Nano logs for hints to that effect and maybe (re)start ssh there with more debugging enabled.
I've had it working with these same devices before, but that was many hard resets ago so I don't remember how I did it.
And dropbear doesn't support anyrhing like verbose mode. It doesn't support -o StrictHostKeyVerification=no either, so I can't use that as a test.
It does support dbclient -y -y, which is much the same. But I still get the same error this way.
-
I've been having some trouble with my router lately. I'm trying to get everything set up for autossh.
If I'm logged in to my router and try to connect to my device, I get this error:
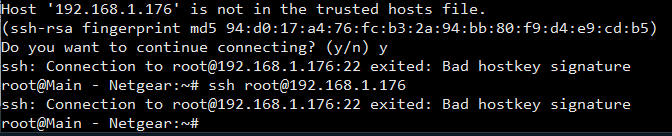
(192.168.1.176 is the Nano)
However, if I'm on my Nano and try connecting to my router, it works perfectly. So it's like a one way connection.
Both devices have all the proper keys added, so no passwords are needed. My router is using SSH-2.0 Dropbear 2014.63, and the pineapple of course uses SSH-2.0 OpenSSH 6.8. The firmware of the router is DD-WRT-v24 sp2 stdP.S. I posted the question here as I don't think it's anything pineapple-specific. Feel free to move it if needed.
-
This should get u started.
Happy hacking!
He basically did everything I did. Almost word for word except the small changes like channel number/bssid/ and wlan1mon.
-
So yesterday it occured to me that I've never actually cracked a WEP network. I've heard that it's extremely easy, so I figured I'd give it a try. From what I was reading I seen you needed clients connected, and they needed to be active. I took an old router with DDWRT on it and dropped it to WEP encryption and added three clients and booted up a Kali live cd.
Step one:
I put my card into monitor mode. (It's the ALFA NEH from the Hak5 store)Step Two:
I ran airodump to start capturing the packets."Airodump-ng -c 1 -w WEP --essid Fallen wlan1mon" (And I also tried everything again using BSSIDs, but no difference.)
Step Three:
Wait for IVs.Step Four:
Speed up the process. A.K.A. Where the problem starts.The first step was to run aireplay-ng -1 0, I believe this is some sort of fake authentication.
I got the message "Sending authorization request" over and over. One had (ACK) beside it, the rest said (OPEN).
Next I needed to run aireplay-ng -3, which was supposed to look for or create ARP packets I believe. Unfortunately, It was showing that it was reading tons of packets, but never found a single ARP request.Considering by this time I only had about 200 IVs, I figured I was doing something wrong. So I decided to use automated tools to see if it worked.
My first try was my beloved Wifite.
"wifite -c 1 -wep -e Fallen"It gets all the way to the actual attack.
Here it tries about seven different types of attacks (Chop-Chop, Fake Authentication, Ect)All of them fail, and by the time it's done I have about 19 IVs.
Just for the heck of it I also tried to use the Fern-wifi-cracker, which wasn't any different.
Thinking maybe it was either y laptop or the card causing the issue, I tried the same steps on my NANO. I used wlan1, and then also tried the NEH again.
Can anyone tell me what I'm doing wrong here? Thanks.
If you need any more information just let me know. -
Unfortunately I've never messed with PHP, so I can't make infusions or modules. But if you don't mind using SSH Wifite is a great way to go.
I've never tried it on the nano but there is also AutoPixieWPS to consider, although it's limited to only pixiedust attacks.
-
I have the S4 and mine works.
Make sure on your settings you don't have the SSID hidden, and that you put it in the list of allowed devices. -
Hi everyone, first post here.
I'm considering buying the nano for a security project at university.
I never used a Pineapple but from what I saw online I'd really like to put my hands on it, also for other experiments aside from the university projects.
What I need (pretty simple):
- I need to log the mac addresses of the clients connected.
I'm sure that the Nano can show the clients connected in real time, but is there a way to store hundreds, thousands of MAC addresses in a log? In other words: is it possible to log the mac address of every client connecting to the nano?
Second question:
Is the Nano fine? Or should I get a Tetra? I'm planning on collecting a very large number of MAC addresses (I will be in a very crowded place).
I need my WiFi radius to be at least 100/150 meters, without obstacles.
Thank You all in advance, looking forward to be part of the community
While the Nano doesn't have 5G or built in amplifiers, I believe it would work fine for this.
You could always use something like kismet from command line, the pineapples have a nice UI that can record things.
I'll upload an example of a report if you'd like.
-
As far as connecting to hotspots, do this.
First connect to the WiFi from the Nano's network page. Then on whichever device you have connected to the Nano, try to browse the internet. On that device it will show the portal.
Example:
Nano is connected to FreeWiFi
My phone is connected to my Nano's APOn my phone, go to www.google.com
The portal page appears, agree to the terms or whatever and click continue.
Now the nano has internet access, and so do the devices connected.
This has worked on every portal I've tried except for one, which used some weird form of mac address tracking. I never could figure out how to make it work correctly. So yes, some may be different, but this should work for most.-
 1
1
-
-
The SSH server I'm using this with has a banner that authentication banner that displays whenever you connect with ssh (Just the standard, "Hey don't mess with this device!" type message). Will autossh still work with this server? If not, is there anything I can do about this, aside from removing the banner? Thanks!
-
....I do not find any other probes from these devices in the logging (eg. probing my home WLAN)?
Any suggestions about this?
I know a lot of devices will stop probing for other networks if they are already connected to one.
-
Samsung Galaxy S4
Stock ROM (Rooted)
It's an AT&T phone, but I'm using it on a different network, so I can only use wifi tethering, not usb.
I use the JuiceSSH app.
-
You need to re-add it to your known hosts. (It's a file in /var/root/.ssh/)I have tried that and for some reason I couldn't connect and I guess all the attempts has locked me out. This is the error message I'm getting.
I've you don't know what this is, and you don't use ssh for anything else, it's probably save to just rename or remove it.
Run this command and try it again.
mv /var/root/.ssh/known_hosts /var/root/.ssh/known_hosts_backup
Whenever you connect to a device with ssh, your computer will save a fingerprint of the device.
This is saying that the fingerprint of the device is different from what it expects, so it's blocking it. (Happens whenever you do a factory reset or something.)
-
autossh -i ~/.ssh/id_rsa.autossh -N -T -R 2022:localhost:22 -R 1472:localhost:1471 <<RELAY USER>>@<<YOUR RELAY IP>> -p 22
just add in an extra route with -R and use the port you want and point it to 1471 the pineapple GUI port. after you add that you can point your browser to your relay server at whatever port you set it at in my case i used 1472 so it would look like
if you are using autossh module. on the command line add it in. and save. it should work from there.
Thank you, adding this to rc.local let it run at boot. (The module doesn't allow you to change the "command to run" itself without editing the .js)
If you want access to the GUI from the Windows machine, I would suggest binding the Pineapple's 1471 to Window's localhost. Configure PuTTY to run the following:
ssh -L 8080:localhost:1471 root@B -p 2222
Then on your windows machine, access localhost:8080.
Some Benefits here over making the Pineapple's 1471 bind to B's 8080 with the -R flag:
- Your interface isn't open and free on the Internet
- Traffic is encrypted "end-to-end". v1.0.5 doesn't have SSL yet
Glad you got it working!
I'll give this a shot, I need to be learning all of this stuff anyways, so here a good excuse for me to do so.
-
Is there a guide on using this somewhere? I'm trying to set this up but I'm a bit of a noob when it comes to this.
I have three devices here.A - Pineapple
B - Ubuntu Server, remotely accessible on port 22 and 2222.
C - Windows desktop with SSH client.
I'm under the impression that I should be able to open my ssh client on A, and connect to B on port 2222 and get a shell on C.
Am I doing this wrong?Whenever I try to connect to B on port 2222, its refused. It seems like nothing is listening on the port.
All of my devices are in each others known hosts/authorized keys, so that shouldn't be a problem.
Here is a picture of my configuration screen on the module, just in case it helps.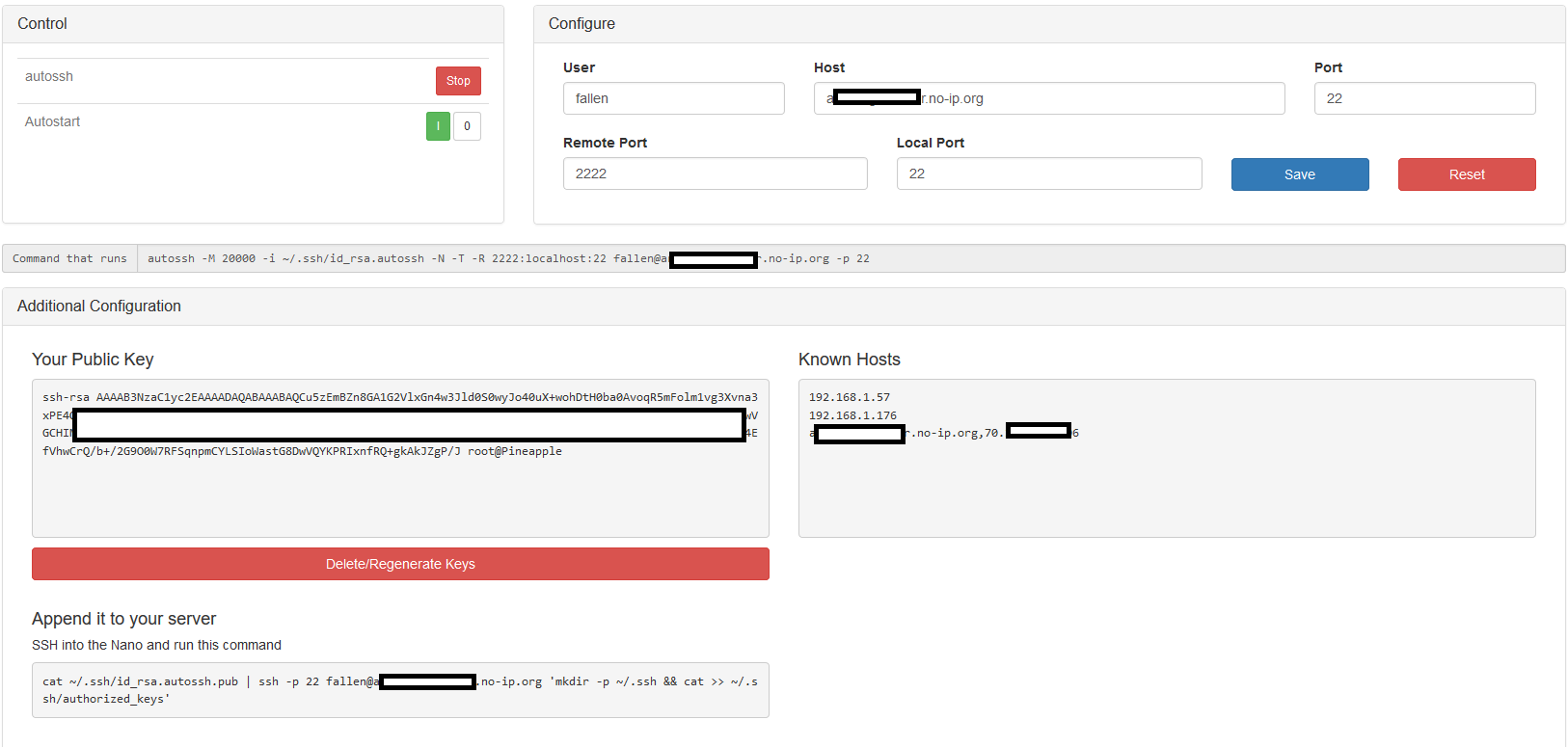
The no-ip.org address is my connection to B.
UPDATE:
I think I get it now.
If I ssh from C (Windows) to B(SSH server) I'm now connected to the middleman sitting in between me and the pineapple.
Then on B, I run 'ssh -p 2222 root@127.0.0.1' and I get access to C (Pineapple).Kinda weird, but I guess it works. Next step if finding out how to get to the pineapple gui from there.
UPDATE UPDATE:A few reboots later and now it's working like I originally though it would?
ssh -p 2222 root@B
connects me to A (Pineapple)
Now I just need to figure out how to get B:8080 to go to A:1471 -
I'm not sure what the correct terminology is here, so I'm having trouble go ogling this.
I want to be able to connect my nano to the internet someplace in china, and then be able to ssh into it from a computer at home. Kind of like a video on hak5 with the Lan turtle.
I have a spare machine I could leave running at home if needed. And I've got a few services such as dyndns that I can point to my home ip.
Can anyone point me in the right direction? Thanks
-
Eww Broadcomm..
Those type of wifi adapters rarely play well in my experience. I've used a tool called ndiswrapper to get wifi working on them in the past. But you won't have things like monitor mode, or master mode. -
I've used USB 3 with no problems. (With the Y cable) Maybe I just got lucky. When I get home I'll check what drivers it's actually using. Maybe windows downloaded then for me.
-
if you dos someone, can they still find you even if you used a vpn?
-
Even if you had permission to do this, you still wouldn't be able to like that for a number of reasons. The biggest one is you simply wouldn't have the bandwidth to pull it off.
Let's use myself as an example. I'm in a semi-urban area, and one of the residents of my house works for our ISP, so we get a pretty high tier for the area. (60mb down, ~6mbs up)For someone to DoS you effectively using LOIC they would need to have an upload speed of around 60mbs. As you can see, that's usually not the case unless you're spending tons of money. If you had ten different computers in ten different locations, you'd have a much higher chance of knocking me offline and out of the call. (Ten different locations, because multiple computers dossing from the same network wouldn't be any different than just using one. In a lot of ways it would be even worse.) Keep in mind, this is only one person, not the entire group.
Adding a VPN to the mix would make things much worse in most cases, as it would even further limit your upload speed.Also keep in mind that this is just generalized, sure your upload speed might be 6mbs, but I doubt 100% of that upload speed is just going to be used for the DoS. You've probably got tons of other devices sucking up your bandwidth, and then the network overhead itself.
This is why DDoS is so common. (Distributed). This is where you get multiple devices on different networks to do the DoS.
And as I mentioned before, I highly doubt you have permission to do this, so know that if you're going to try it anyways a vpn will not save you. If they really wanted to, a quick call to Hotspot Shield from your school, perhaps with the police involved, would provide them not only with your real IP, but also whatever information you used to sign up.

-
Working my way from the bottom up, this was at line 1170....it looks like your machine went to sleep...
[ 8525.857200] ACPI: Preparing to enter system sleep state S3
Also, if you're using a laptop with kali, closing the lid will cause the system to sleep unless you edit one of the configuration files.
Open /etc/systemd/logind.conf and change the line that says "# HandleLidSwitch=sleep" to "HandleLidSwitch=ignore". Then either restart your system or restart run:
systemctl restart systemd-logind
-
Two weeks from now I'll get paid and I'll be able to finally buy the Nano. But since I don't want to wait that long and I have a spare laptop laying around, I figured I'd put this here until then. Basically I have a laptop and I want a Nano Tactical Edition. I feel that the price of the a Nano Tactical Edition and shipping for a small laptop is worth it for the laptop, but if you disagree then no hard feelings.
Laptop Details:
HP ProBook 455 G1
300Gb Harddrive
4Gb RAM
AMD A4 Processor (2.7)
AMD Radeon 8350G
Supports Monitor Mode (b/g/n) (RTL8188EE rev1)
Fingerprint Scanner
Webcam/Mic
Numberpad
SD card reader
HDMI Out
VGA Out
Ethernet
4x USB
Mic/Headphone Jacks
Kingston Port
The only thing to worry about condition-wise is a few stickers I have on the outside. I'd take them off, but removing stickers without tearing isn't I skill I'm good at.
Comes with a license for windows 7 home premium, and it was part of the one year free upgrade so you can also install windows 10 if you choose to and the license will work. I'll be wiping it before hand, but if you need an installation disk for either of those, or of something like Kali, I can provide that as well. I have a sleeve for it, and of course a charger.
I'm located in Oklahoma. I've shipped a similar laptop from the Arkansas/Oklahoma border to Nevada and it cost almost exactly $20 through USPS, so that should give you an idea of the shipping.
Images:


-
Hello,
I recently changed my email and password, and since then I'll get randomly logged out of the website. Other times I'll be asked to log in, and when I do I'll be given an error because I'm already logged in.
I've tried manually logging out and back in, and I've cleaned my cookies and everything, although I doubt this is the problem since it happens on all of my devices.
Just a minor inconvenience, I'm mainly just worried of getting locked out all together. Anything I can do to fix this? Thanks.




Bash Bunny vs Packet Squirrel
in Questions
Posted
Hello, I haven't been around for a while and I'm interested in purchasing either Bash Bunny or Packet Squirrel devices. I'm not sure which would fit my needs better. I'm mainly wanting to be able to drop this device and use get a remote VPN/SSH connection.
I'm just an amature messing with these devices for fun, so I feel like the packet squirrel can do this in a much more user friendly way. And it has expandable storage which is a big plus. Looking through the payloads on GitHub, I noticed the I Hate WiFi one is using wlan0, but I'm not able to find any mention of it having wireless onboard
The Bash Bunny also has rubber ducky like capabilities, and only requires a USB port. As far as I'm aware there is not expandable storage options, but if it can create a VPN/SSH session I wouldn't mind losing that.
I'm not concerned about the price difference, so I think my main question is if the bash bunny can create a VPN/SSH tunnel, and if there would be any benefit to getting one over the other for this purpose. Lastly, I'm wondering if the packet squirrel has wireless, or a USB port to add a USB adapter. I like the other things the bash bunny offers, but I'm mainly focused on remote access.
Thank you for reading all of this.