
factgasm
-
Posts
117 -
Joined
-
Last visited
-
Days Won
1
Posts posted by factgasm
-
-
-
I have just upgraded to 3.0.0.
It's a lovely lovely new look, it must be said.
However still no interfaces showing on the Interface dropdown box of the Wifi Client Mode section. Please help!
Is there some command I can issue in the Pineapple's command line I can enter to refresh the interfaces so they show?
It is as if a file containing the list of interfaces has been corrupted, but I don't know which file. Please help!
-
Seriously would appreciate some help on this.
In Recon mode the Pineapple picks up the ESSID for my home wifi but still no interfaces showing on the Client Mode tab of the Network tile. Please help!
-
On the home page click on Network and then the Client Mode tab.
Where it says "Join A Network" click Scan.
Now pick an access point from that list and enter the password just beneath.
Once joined, go back to the homepage and refresh the Network tab. Should be a-OK.
-
Mk5 using firmware version 2.4.0.
Did a remote deploy last night. Pineapple was taped up with gaffer tape to protect it from the weather, so no sockets or plugs were exposed whatsoever. We had a torrential thunder storm about two hours after deployment. Got it home this morning, dried off the few drops on it. Opened the pineapple casing - it was bone dry inside. I was able to connect to it from my phone, and from my laptop I could shell in and WinSCP in too, but something didn't seem right about it.
Did a factory reset. All four lights, green,yellow, blue, red flashed. Good. Then went to do some basic set up.
Went into the Network tile, clicked Client Mode and clicked on the dropdown box next to Interface. There were no interfaces showing and have not been showing since. Please help.
I have followed the suggestions on this thread. Shelling in and running the cat /etc/config/wireless from the command line showed no reference to radio1 at all, however an ifconfig shows reference to wlan0 and wlan0-1.
PS I have just run iwlist wlan0 scanning and iwlist wlan0-1 scanning and both are picking up the ESSID for my home wifi so it appears both radios survived the weather but still no interfaces showing on the Client Mode tab of the Network tile. Please help!
-
Fixed! (see below).
I have been following frozenjava's excellent Evil Portal videos on Youtube. I have a Pineapple Mk5 running the latest firmware and I have a question for the forum.
I watched both the "How to Setup Evil Portal 2.x" and "Getting Credentials with Evil Portal" videos and these were very clear indeed.
The Evil Portal infusion is now running and I have editted the code to capture a username and password. I know that frozenjava's HTML and Javascript code works because stepped through it using Visual Studio's debugger. However I think Evil Portal needs some port configuration done to it because so far in testing it, the username and password are not being recorded to the stored.txt file.
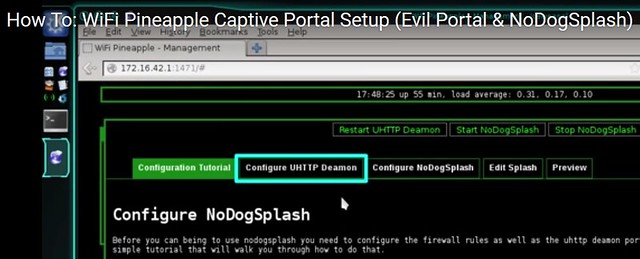
In Chris Haralson's video "How To: WiFi Pineapple Captive Portal Setup (Evil Portal & NoDogSplash)" he refers to an earlier version of EvilPortal and talks about Configuring UHTTP Daemon. (Go to exactly 3 minutes in).
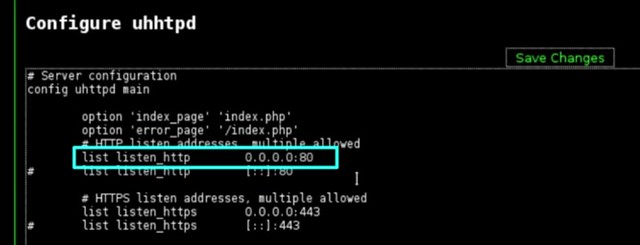
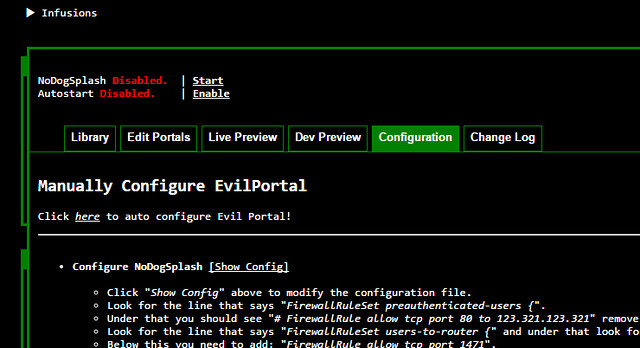
At that point he edits a line "list listen http 0.0.0.0:80" and he changes the 80 to read 8080. That is the port number used in frozenjava's code. The problem is that in the Evil Portal 2.4 version - which I have installed on my Mk5 Pineapple - there is no button to click for configuring the UHTTP Daemon.
Does that editing need to be done in Evil Portal version 2.4? Do I need to edit the list listen_http value to 8080? Please help!
Evil Portal GUI from earlier version showing option to Configure UHTTP Daemon:
list listen_http being editted as shown by Chris Haralson:
Evil Portal GUI from current version (August 2016) without option to Configure UHTTP Daemon:
Fixed! Explanation:
frozenjava's Youtube video was recorded using an earlier version of the Evil Portal infusion which used port 8080, hence the reason 8080 is embedded in the javascript.
However version 2.4 of Evil Portal runs on port 80 instead. For proof just see below:
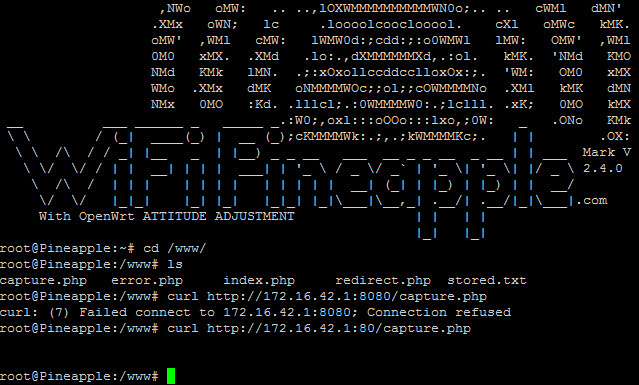
Note that the command curl http://172.16.42.1:8080/capture.php - which should cause the capture.php file to execute, - fails because the connection on port 8080 is refused.
However, the command curl http://172.16.42.1:80/capture.php successfully causes the capture.php file to execute just fine.
Quite simply, if you want to adapt frozenjava's code for your own Evil Portal (v2.4), make sure to change the port number from 8080 to 80. That's it, couldn't be simpler.
I am a very happy bunny.
-
No, I think you are confusing vengeance with justice and since when is using a gun or knife the only way to seek revenge?
Cooper has stated already that by using the Pineapple to get evidence you are tampering with it. With that you are committing a crime yourself. It doesn't matter if someone wronged you, if you illegally access their systems/networks/etc you are at fault for your own crimes.
I'll say this again, if you want to interface to be different quit trying to use emotional tactics on us. Instead, change it yourself in the CSS Editor tab of the configuration infusion. You can find all of the other files for the interface in /pineapple/includes/. When you're satisfied with what you've built you can present it to everyone here. Until then everyone is going to continue to use the current interface because it's effective and serves its purpose for the community.
Its the Pineapple we deserve, but not the one we need right now.
-
I see 2 problems with that long post you made.
1. Against all the criminal acts you mentioned the Pineapple cannot help you at all. It can't protect you from it, it can't help you defend yourself during the act aside from maybe using it to beat your assailant over the head with it, and I'm sure there are plenty more appropriate, sturdier and heavier tools around for that. Maybe poke someone in the eye with an antenna, but that's pretty much it. After the fact you can't use one to make you feel more safe or less violated because, as I already mentioned, it can't help prevent a re-occurrence.
2. When you hack a someone who you consider to be a criminal (innocent until proven guilty and all) to gather evidence, you're doing the exact opposite: you're tampering with evidence. If you produce some document or email to an investigator, that investigator needs to take into account that you may have fabricated the document, so you need to say where you got it from. If you got it from the supposed perpetrator's harddrive, that would prove you have access to that drive so all data on there is now tainted. After all, you could just as easily have planted this evidence as well as any other file that might be indicative of criminal behaviour (child porn pictures, say). To make matters worse, hacking someone's machine without consent is illegal meaning that when you provide the document to a detective, you have proven yourself to have broken the law whereas the other guy is just some random and, thus far according to the law, completely innocent citizen.
You know how it is that criminals succeed? They have no rules. None. They have no feeling or concern whatsoever for what they do. There's no angst, no inhibition, no anxiety, no remorse, they just do . . . . things. They'll break every rule in the book and feel no concern whatsoever for the harm they are doing.
I tell ya this, if I had to hack a criminal to bring his criminal rampage to an end and to stop him destroying more lives, let's just say that sometimes structures become shackles, letting the bad guy get ahead.
"I have foresworn myself. I have broken every law I have sworn to uphold, I have become what I beheld and I am content that I have done right!" Elliot Ness, The Untouchables.
-
You, sir, need to calm your tits.
And after you've washed your mouth out, you need to meet some victims of crime and see what damage crime did to their lives.
-
Nope, I know how to defend myself, was an instructor for many years. It just looked like too many other magic jellybean fix all your problems infomercials you see on late night television. Nothing you wrote can be fixed with a wifi pineapple. That's not it's purpose, and anything you do use it for won't be admissible in court anyway. It's not your job to gather evidence, it's the police's job.
Fight training will only defend you in certain circumstances. For example, some asshole shoots your wife dead in a drive by? Or someone deliberately tries to run you down on the sidewalk late at night with a motorbike because they know you've rumbled what they're doing. What you gonna do now? How exactly does pulling a Bruce Lee pose help you in those circumstances? Too late.
Now suppose that the criminal rather than posing a physical threat poses a white collar threat, for example, bribing senior local officials in return for cooperation with plans for some new toxic industrial installation - which could lead to hundreds, even thousands of deaths.
In either case you can't go into a court and tell the judge "Here's a bunch of documents proving the accused is guilty. I got them by hacking his computer" instead you pass on the information to the authorities and, hopefully, they go get the warrant if not you go to the media and if they're turning a blind eye.
-
That is the biggest load of bullshit I've seen in these forums.
Suppose you'd been victim of some of the crimes I mentioned above. What would you do, lash out, like you just did? You can't even control yourself over a post.
-
What your suggesting is that the Pineapple be made into an easy tool for vengeance rather than justice. The unanimous point remains that the Pineapple is a penetration testing tool. It is not for vindictive business men as one of your examples displays. I understand some of your reasoning, however, simply changing the user interface will not bring the average user to a greater understanding of the technology beneath. Without the understanding of what is actually happening they will not be successful in their personal vendettas but instead will be out $99. If the interface bothers you so much change it yourself. After all, Hak5 has given you the opportunity to do so in the Configuration infusion. When you build your ideal interface post the CSS on here and see what people think.
The fact that you suggested I was implying the Pineapple be used for vengeance shows you didn't read what I said correctly. I made it very clear that using a gun or a knife - which would constitute vengeance - is the neanderthal approach. The smart approach is to uncover information the criminal would prefer was kept secret and you do that by hacking him.
Suppose you suspected someone was committing serious crime but lacked the evidence to prove it. Now suppose you came by information that could be used be used to bring them to justice, would you use it or would you just turn a blind eye?
-
And you're not seeing the potential.
Everyday right across the globe the lives of millions of innocent people are damaged or destroyed by criminals who very often go unpunished and remain free to continue their spree. Sadistic, predatorial criminals who commit premeditated acts such as threatening behaviour, harassment, fraud, theft, extortion, rape, assault, human trafficking, drug dealing, embezzlement, sexual slavery or murder - among others.
Naively, many people trust that, because they are good themselves, should they ever become a victim of crime the criminal justice system will leap to their defence and put everything right. The reality is that the criminal justice system has finite resources, works strictly by procedures and is slow to act ("You have all these rules and you think they'll save you.") Worse still, its officers can be judgemental, prejudiced and even corrupt ("Moroni's men") thus denying the victim justice at the first hurdle.
Victims of crime often struggle to convince the police that a criminal act has occurred at all, because they lack a vital piece of evidence. An email here or a document there could have made all the difference. ("Well, it's not you know, it's what you can prove in court. Didn't you tell me that once?" as the great Clyde Shelton once said).
Even when there is sufficient evidence and a prosecution goes to court the criminal will often avoid the full extent of the punishment they deserve because legal procedures have resulted in compromise. The criminal justice system's failure to prosecute criminals only adds insult to a victim's sense of injustice.
Right now, at this very instant, right throughout the world, there are millions of people living with the hurt not just inflicted on them by the criminal, but by the system's subsequent failure too - and what do they do then? The inconsolable widower whose wife took her own life after being raped. The loving parents whose child was abducted and murdered by a paedophile ring. The elderly widow defrauded of her life savings. The moral entrepreneur contemplating suicide after being defrauded by immoral business partners.
What do these victims do when the system fails them? Learn to hide the anger behind a smile? Get a knife or a gun and turn on it themselves to end the pain? Or turn vigilante and kill the MF?
Unlike Clyde Shelton, most ordinary people, Mom and Pop if you will, are not CIA assassins and they're not hackers either, they're just good, ordinary people, law abiding citizens who happily went about their lives unwittingly stood in the path of the tornado.
Most victims of crime have not spent their prior lifetime with Linux or attending DefCon or learning aircrack or hacking their neighbours wifi from the safety of their own Mom and Pop's house, but don't deserve to be cut off from getting justice for themselves just because of that.
Occasionally, when people suffer appalling injustice, they take power into their own hands and resort to weapons like knives and guns. Using a weapon might satisfy your bloodlust but they can get you a prison sentence. That's how justice (or injustice) works.
The Pineapple has the potential to empower victims of crime to uncover vital clues that the system failed to find, evidence that could see the criminal finally sent to prison. For instance it could help uncover the whereabouts of stolen money, uncover conspiracy or uncover details of the criminal's next hit. Sending the criminal to prison also has the potential to end a whole wave of serious crime and spare others the misery they may have otherwise suffered.
While the Pineapple has this potential, its interface is set up so that only those who have developed a high level of expertise can make of use it. That's why I implore Hak5 to produce an improved user interface so everyone can make use of it. Please don't keep the Pineapple the play thing of an highly specialist in-group, bring it out into the sunshine and help let justice prevail.
"I'm still a believer in Pineapple even if you're not."
-
That's exactly the same arrogant attitude Microsoft took about ten years. Like IBM before them they were convinced of their invincibility. They used to define an entire industry but they failed to notice developments elsewhere and missed out on the emergence of entire whole new markets. What's Microsoft's share of the smart phone and tablet market?
Three days ago Apple reported the biggest corporate profit in history. Remind me now, what is it that Apple is famous for?
Make the Pineapple's interface slicker and more intuitive and you'll sell a lot more and just think what interesting new projects Hak5 could fund from extra revenue.
-
Even when I cut the file down to containing just the single solitary password for particular accounts I am attacking, even then Hydra fails.
I seem to remember when I was setting up some of these accounts that Google offered an option to add increased security. On some of my accounts I opted for that security, on others not.
It would seem that Hydra is having difficulty with the accounts that I opted to have extra security on.
-
Over the last twelve months or so I have created numerous gmail accounts for myself for different purposes (for example I tend to use factgasm on forums). Today I have been trying out Hydra for real, namely hacking my own gmail accounts.
I set up a very small password file containing a range of random passwords and passwords to my gmail accounts.
I then ran hydra using the string:
hydra -s 465 -S -v -V -l [gmail address] -P [passwordfilename.txt] -e ns -t 16 -F smtp.gmail.com smtp
Weirdly hydra does find the password for some of my accounts but not others. Anyone else ever come across this?
-
From that video, around the 1:50 mark: "I'm trying to position ReaverPro to be useful for mom and dad."
If you're wondering why the Pineapple's presentation is different, there's your answer.
The Reaver Pro's presentation isn't just different, it's excellent.
If the Pineapple's presentation was as good, Hak5 would have a bigger market to sell to and they'd sell many more.
-
Reaver Pro's new user interface is absolutely superb. Terry Dunlap is master of presentation. If only he would work his magic on the Pineapple which frankly, in terms of presentation, is lagging way behind.
What Terry does is to take complex information and present it so everyone can understand it and that's how the Pineapple should be too.
https://forums.reaversystems.com/index.php?threads/using-the-new-reaver-pro%E2%84%A2-interface.41/
-
That's weird, Mr Gray. Your avatar seems to have aged while you have haven't.
???
(That's Dorian Gray from the League of Extraordinary Gentlemen, if I'm being too cryptic)
-
I'm changing my original post because now I've put my pen testing hat back on all this is making a lot more sense now.
I downloaded the file again, this time directly from crackstation itself, unzipped it, managed to open it and it is indeed plain text after all.
It's possible the version I had earlier was corrupt hence the confusion.
-
Thanks Cooper.
Andrew sure knows what he is doing and his videos are superb, but does he sell ready made antennas? I really need an off the shelf solution, not something I would have to build myself as I have already wasted enough money and time on other self-build projects in the recent past. Is there a tried and tested ready-built solution someone can recommend on say ebay?
I like the idea of a Yagi In A Can because it looks discrete. It could be a poster or a canvas painting rolled in a tube up for all anybody else would know - and therefore not likely to arouse suspicion.
-
Suppose you were out in the field, trying to connect to your target's wifi. You cannot go into the building, at best you can park in a vehicle out on the street.
What antenna would you recommend and why?
-
Dear oh dear oh dear:
You might want to see some comments by yours truly at the bottom of that page (pffffft!)
I wondered if folks on this forum could contribute their own?
-
Hey Oli,
Can the Peensy be disguised as an ordinary USB stick?

Error connecting. Please check your WiFi Pineapple's internet connection.
in WiFi Pineapple Mark V
Posted · Edited by factgasm
genxint, did this work for you?
By the way, you can now update your MK5 to firmware version 3.0.0 by clicking on the post below: