-
Posts
242 -
Joined
-
Last visited
-
Days Won
1
Posts posted by nopenopenope
-
-
I just like digip's comment in the beginning of this post. "Do it for the hack" I think we need to make shirts.
-
Dual core of course.
Anything by Jack White
Cage the elephant
Nirvana
Breaking benjamin
Fun
The last dinosaurs
The limousines
Modest mouse
Three days grace
Marilyn mason
Manchester orchestra
Imagine dragons
Skrillex
10 Years
Billy tallent
Beck
Cake
Awolnation
Mgmt
Morning parade
Black keys
Bob dylan
Beatles
Mumford and sons
Naken and famous
Neon trees
My darkest days
Passion pit
Rise against
Hollywood undead
Ya... a little bit of everything
-
I still don't get the point of mapping this. Cop cars move. Just get a good radar detector and don't go more than 15% over the speed limit and you'll be fine. If your going 100 in a 55 you'll still get caught no matter how good your radar detector is. Go to the boonies and have your fun ;)
-
How would you make it better, its a brute force script, you can only go as fast as the router will let you, and reaver does that. You could gather a list of preset WPS keys, but I think you can select an option in Reaver to do that.
-
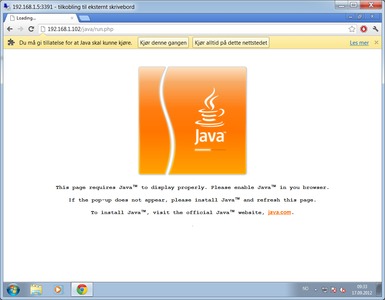
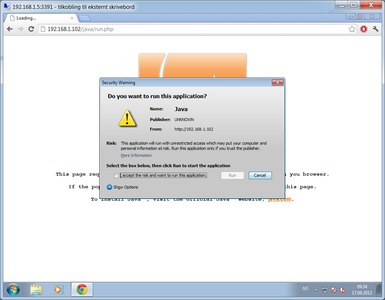
I'm afraid this is easier said than done.. I have no knowledge about this at all, but I'll bet that Oracle protects their signed java applets as good as they can.. However the java client on users computers is breached every now and then.. <_<
In my opinion I think most (normal) users have some kind of AV that the computer was originally delivered with, maybe not very god ones, but nevertheless I think that any attacks/pentests should be as stealth as possible i.e. no alert in AV.
People that are not using AV would be more aware and not install an applet like the one above, and user not aware would be aware because of the AV.
Ya I was completely kidding. No way would you ever want to do this on a Pentest, Unless you want Oracle to come down on you like a ton of bricks.
-
I have played a little bit with the Evil Java applet and found that the possibility to lure someone is quite slim.. The user would have to be quite braindead for you to achieve the attack.
Just to make it clear I did not start a listener in Metasploit, nor did I test this in the "right side" of the pineapple. The reason for this is both that I'm not sure how to change the listener address in the attack, and I didn't want to create a BT VM in my laptop for this test.
This test is made from the WAN/LAN side. And MSE went totally crazy when I entered this site, so the test is run without any AV.
Firstly the site is.. well not too bad
But the warning speaks for itself
Especially when the AV is amok at this point.
That said, I have also tested a couple of java attacks from SET in backtrack, but I haven't found any that actually fools MSE. If anyone have any tips to what java attacks one might use without AV going insane would be great! Otherwise I don't see any point in using time on this.
In regards to what you can do with it is potentially own the users machine ;)
Get the executable signed by java/oracle :P
-
-
There's tons of viri out there that delete it's traces or will uninstall itself if it detects a debugger running. Why does that have to come from a government? I'm new in the game, but from what I've read that's an old trick. The wiki article says it infected 1000 machines. I bet there are people on this board who have pwned more boxes than that with a single method.
Kaspersky does make one of the better antiviruses, but after seeing their interviews and meeting one of them face to face I lost a lot of respect. They're like Russian cheerleaders for viri.
Well thats basic yes, but the update system, crypto, and root kits in it all new technology, not the ideas themselves but how they were implemented. the code dates back to 2007, and stuxnet and doqu where just "modules" to the flame worm. The worm itself supports everything imaginable. Its pretty much its own OS running in the background. Im not entirely sure on how the code signing worked but if you listen to those links i posted the developers had to go to incredible lengths to crack the crypto for the code signing. Flame is the most advanced worm to ever exist, and who knows what else it did and was capable of. 1000 machines were specifically targeted, it had a specific job. Iranian government was infected with this thing for 5 years and was undetected thats an incredible acomplishment.
-
There are only speculations, but the evidence isn't that solid. They still don't know who's really behind all these events. I've also read that the US President Barack Obama is behind all these Cyber-attacks. One thing for sure, is that these authors are certainly sponsored by the government.
First was Stuxnet, then Duqu now Flame what next. I think there is more to come.
Especially since there were several zero-days involved in flame, one that involved getting the code signed by microsoft, and flame exploits the windows update system with that and updates the malware within that. Several hours after it was first reported in romoved all traces of its self from the hard drives and then wrote over that space to ensure there wouldnt be any forensic evidence. And alll the data sent to and from the CC servers was encrypted serveral different ways. I'd love to see the source code of this, kasperski stated that it would probably take 10 years to reverse engineer the whole thing.
-
http://www.grc.com/securitynow.htm Episode 355 and 357, Stuxnet seems to be wrote by the same authors as the newly found Flame Virus, its also thought to be a module for the Flame, this thing is sick, and the amount of effort put into this had to be Governmental and probably part of the 'Olympic Games'
http://www.nytimes.com/2012/06/01/world/middleeast/obama-ordered-wave-of-cyberattacks-against-iran.html?pagewanted=all , The Flame virus was originally thought to be written by a different group than Stuxnet ( http://www.crysys.hu/skywiper/skywiper.pdf Was first called skywiper by crysys, but a module in the reverse engineering process found a module called flame, therefore the new name.) but is now looking like its from the same author(s)http://www.forbes.com/sites/kenrapoza/2012/06/11/kaspersky-lab-same-countries-behind-stuxnet-and-flame-malware/. I've been following this for the last week and its really really interesting. I'd listen to those 2 episodes of that podcast if you want to know more about how it works.
There's still no proof that this was done by the US or Israel. I just find the technology behind it incredibly interesting. Makes me want to go into malware analysis lol.
-
Get a prepaid card, buy you self an server in a different country. VPN, Proxy, SSH, and TOR it. VPN, Proxy, SSH, and TOR yourself. And connect to it and a large open hotspot never in the same location preferably in another state lol. University's would work well because they have a lot of traffic, Change your MAC address. Do what you need to, toss the laptop, then GPS, WIFI, 3g, 4g, cellular, Radar, and Sonar Jam you self home, and take the back roads. Before you do all this, cut off all communications with your friends and family, several years prior to doing this. Don't have any sort of prior record (They might be keeping tabs on you), and never use credit cards. Then move to a 3rd world country with no expedition laws and never think, or speak of it.
Even something as far fetched as this, if some one has the resources and really wants to find you, and what you've done, they will. No one has true anonymity. Will you get caught, probably not. But nothing is hole proof, hackers should know this best, we're the ones who make the holes.
-
By the time you get that far, there's no reason to change anything on the router. unless you want to own EVERYTHING, but that's going to throw up major red flags.
Besides by that time you can already do what you need to within the network and have done one of the following to get there;
1. Your internal and you can exploit / mess with what you want
2. you've exploited something now your in and you can pivot by exploiting, arp /dns spoofing
3. you've social engineered, whether or not they've installed something, put in a flash drive, or got phished, etc, etc.
4. You broke or snuck in, in order to compromise the network.
I guess it really depends on what your after, or what your trying to present (as you've mentioned) to go as far as the router your demonstrating how to completely disrupt the company's operations. If your showing them how some one can gain valuable information, you're better off leaving the router alone, and targeting a select few machines to keep things quiet.
On a somewhat related subject, I've never really seen the point with touching the networks routers, unless you need to in order to pivot / maneuver through the network, and unless you're out to disrupt the company's operations (you might as well just DOS it then though). Is there any reason I'm not seeing where you'd want to actually mess with routers? I'm not talking wireless here.
-
All I can say is make sure your VM is set up as bridged, (I keep the 'Replicate physical network connection state' option checked), Use windows xp service pack 2. Make sure you select a payload, the exploit may complete, but if there's no payload to upload once it completes you won't be able to get a session.
First try pinging your windows xp machine, if you can't, you have some other network issue, it could be your VM settings, or your normal network settings. Once your able to "see" the victim machine, try using metasploit again.
If you still have issues with metasploit after you can "see" your victim machine, post your complete inputs and outputs from start to end of what your doing in metasploit, and I'll see if I can help.
-
If your new to nmap you can;
1. Do what Mr. Protocol said.
2. Use Zenmap and use some of the default settings, and read the commands, and play.
-
For my mods that need batteries, I use these: http://www.energizerpowerpacks.com/us/products/xp8000/
I also modded my daughters Airhogs Heli and Car to charge off these as well.
They are super useful!
I might have to add the pineapple to my cuurent "black box" that houses my AIRPCAP NX and my ALFA.
Lol your daughters charger... "Dad, can I use my charger? I want to play with my car" "No! Go to your room! I'm haxoring!"
Nice mod, I'm still working on mine, I'm trying to figure out a charging cycle for my lith-ion's.
also, I like the metasploit book in the background.
-
I suggest centering pictures with css instead of html.
-
I dont like yamas, checkout easy-creds, since it has a soft AP option in the script, i feel as if it would be more suitable for running on the pineapple.
-
If you want to build yourself a batter pack HERE is a PCB 7.2v Circuit Protection board if you are using unprotected 18650's or the like.
Used them in a number of other projects and they worked great!
so the battery's go in on B-/B+ and you charge/use on P+/P- ? thats it?
I might get this, but the protected batteries are the same price so we'll see.
-
The cells won't have any protection inside them.
Crap. Thanks, I'll buy some with protected cicuits.
-
The battery packs have the protection circuit in them.
This is the inside of a Powerbook G4 battery. The circuit is in the upper right of the pack. There's also a thermister sitting between a couple of the cells for overheat protection.
I don't have a battery pack like this, I literally took a dremel to my old laptop battery, and I'm using the cells individually. without any external circuitry, I'm wondering if they have a protection cicuit inside them.
-
I think I'm just going to buy this http://www.amazon.com/18650-Rechargeable-Li-Ion-Battery-Charger/dp/B004B1BR24/ref=sr_1_6?s=electronics&ie=UTF8&qid=1331247091&sr=1-6 , put the 2 slots in series, then make an adapter for my plug I have on my new case I've made (I'll post picture soon) but my pack has 6 batteries, 2 sets of 3 in parellel, and then those to sets in series. So when I charge them, should I charge them 3 times? because these are Lith-Ion batteries, the charger should have a timed cut off, so the batteries aren't ruined.
Also, I know that some lith-ion batteries have the protection circuit in them, would the ones out of a laptop have those in them?
I found this http://www.amazon.com/Tenergy-Protected-Cylindrical-rechargeable-batteries/dp/B001C1WMMU/ref=sr_1_38?s=electronics&ie=UTF8&qid=1331248249&sr=1-38 (not concerned about the product, just the pictures) My batteries are coated like the ones in the picure, (with no markings), would it be safe to assume that they have the protection circuit like the ones in the other picute on that product?
-
Darren, i have my old laptop battery safely disassembled, and am setting them up for pineapple awesomeness. How do i charge them after? Safely?
-
Another funny battery story - I was at work moving around some of our wet-cell batteries, testing some sensors or something. I went out to lunch with a couple of girls to subway where one of them dumped her cup of water. It covered the table and dripped down onto all our laps. Funny funny, insert "we all peed ourselves" jokes, blah blah. Well little did I know that I had inadvertently gotten a rather massive amount of battery acid on my pants when moving them, so when introduced to a nice base such as water - they removed the fabric from my pants. All I had left, when we stood up to leave, was from the knee down and the belt portion of my pants. Hilarity ensued.
telot
lol damn battery's
This sort of thing happened to me carrying a cracked troling motor battery when going fishing when I was like 14, I didn't loose as much of my pants as you, but it looked like my right leg got hit with a round of bird shot.
-
yup, just used an direct image location from some site wherever (found on google images) and embeded a youtube Iframe for the video i wanted. then just wrote the page. copy the code into a notepad txt file and save it as whatever.html and view it in your browser if you want to play with it.






Square reader hacks
in Everything Else
Posted
Google, the info is publicly available. Not going to tell you how to do that.